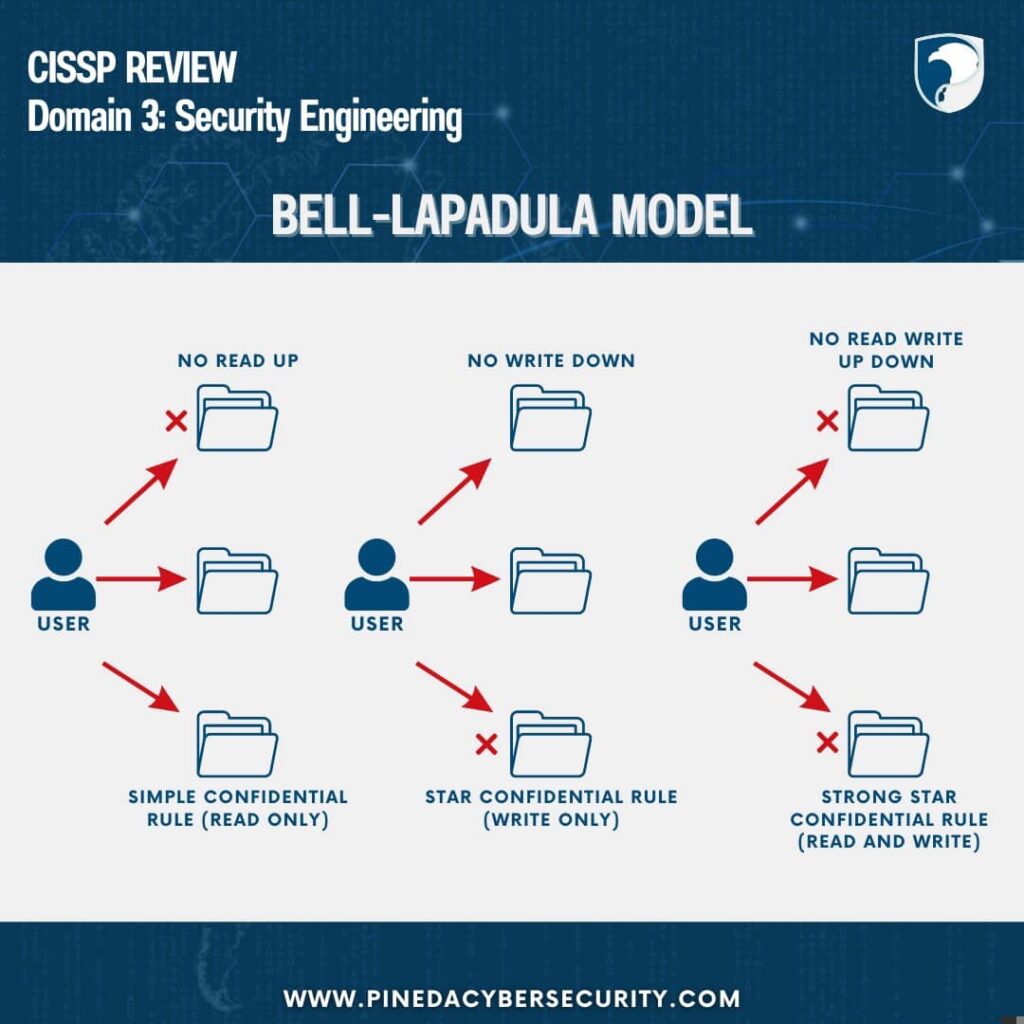
1)Bell-LaPadula Model
Simple Confidentiality Rule:Subjects can read files on the same or lower secrecy layers, but not higher ones (“No Read Up”).
Star Confidentiality Rule:Subjects can write to files on the same or higher secrecy layers, but not lower ones (“No Write Down”).
Strong Star Confidentiality Rule:Subjects can only read and write files on the same secrecy layer (“No Read Write Up Down”).
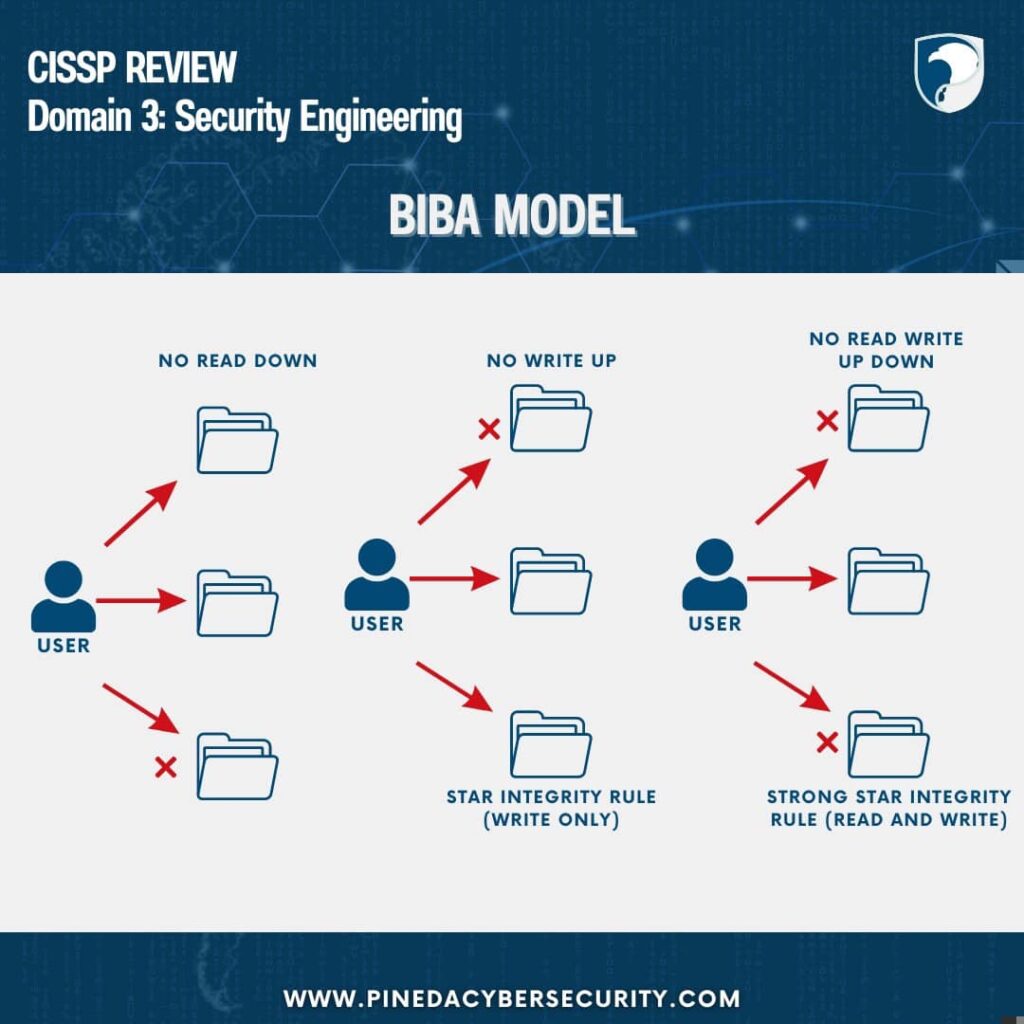
2)Biba Model
Simple Integrity Rule:Subjects can read files on the same or higher integrity layers, but not lower ones (“No Read Down”).
Star Integrity Rule:Subjects can write to files on the same or lower integrity layers, but not higher ones (“No Write Up”).
Strong Star Integrity Rule:Subjects can only read and write files on the same integrity layer (“No Read Write Up Down”).
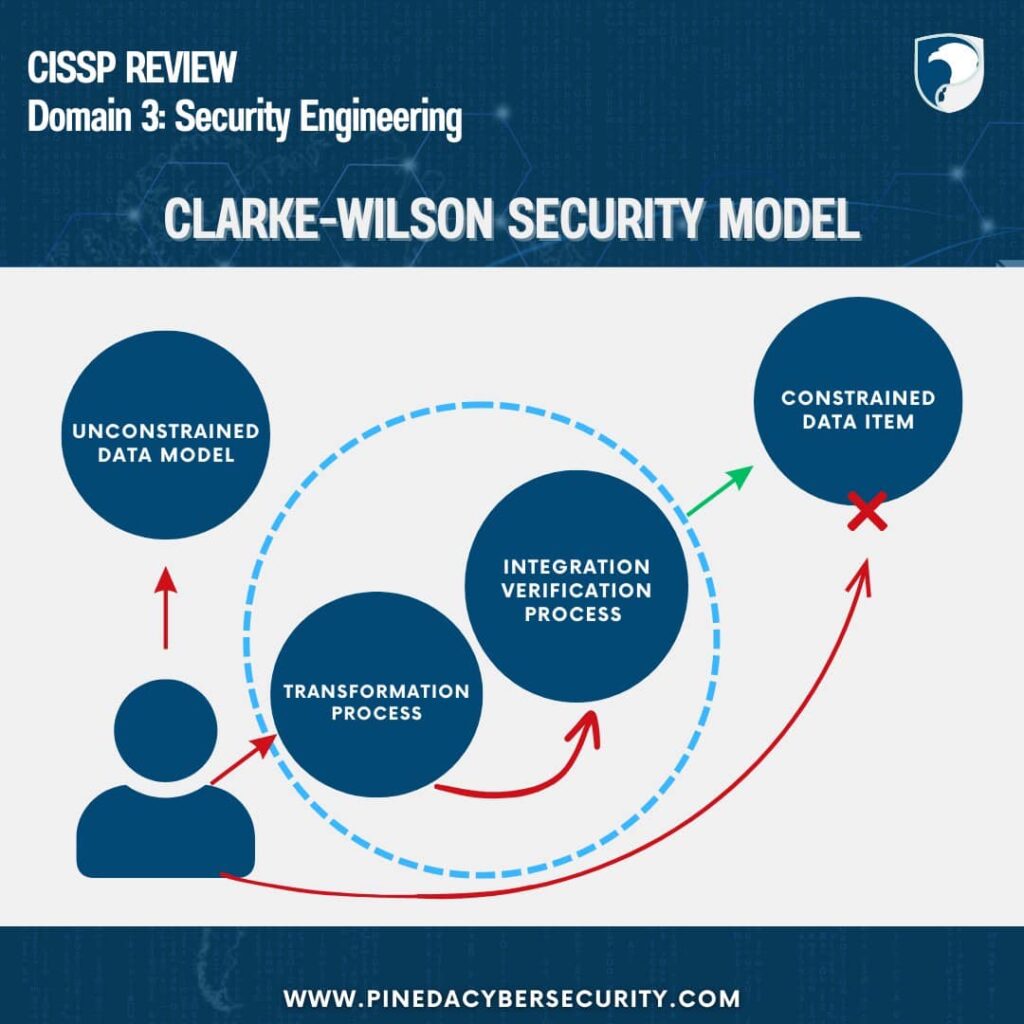
3)Clarke-Wilson Model
Subject:Any user requesting data.
Constrained Data Items:Data that must be accessed via a transformation process.
Transformation Process:Handles access requests and converts them into permissions.
Integration Verification Process:Performs authentication and authorization before granting access to constrained data items.
These models help in structuring security protocols to ensure that information remains confidential, maintains its integrity, and is available to authorized users.
#PinedaCyberSecurity #CyberSecurityMakesSenseHere #CyberSecurity #DataProtection #Confidentiality #Integrity #Availability #SecurityModels #AccessControl #BellLaPadula #BibaModel #ClarkeWilson