
by PCS | Jan 26, 2025 | 2025, Tips & Tricks
An IDS plays a vital role in your organization’s defense strategy by monitoring network traffic for suspicious activity. It alerts administrators to potential intrusions, enabling swift responses to mitigate risks. While considered passive, its real-time...

by PCS | Jan 26, 2025 | 2025, Tips & Tricks
Mastering these security control categories is crucial for a well-rounded cybersecurity defense. Start building a resilient security posture by understanding how these layers work together to protect data and infrastructure! #PinedaCyberSecurity...

by PCS | Jan 26, 2025 | 2025, Tips & Tricks
From small startups to global enterprises, no business is immune to cyber risks. Understanding information security risks is crucial to safeguarding your business operations and maintaining customer trust. At Pineda Cybersecurity, we empower businesses to navigate...

by PCS | Jan 26, 2025 | 2025, Tips & Tricks
Cybersecurity Starts at the Top! In today’s digital world, cybersecurity is every executive’s responsibility. Are you doing enough to protect your company from cyber threats? Discover actionable steps to strengthen your organization’s defenses. Understand your...
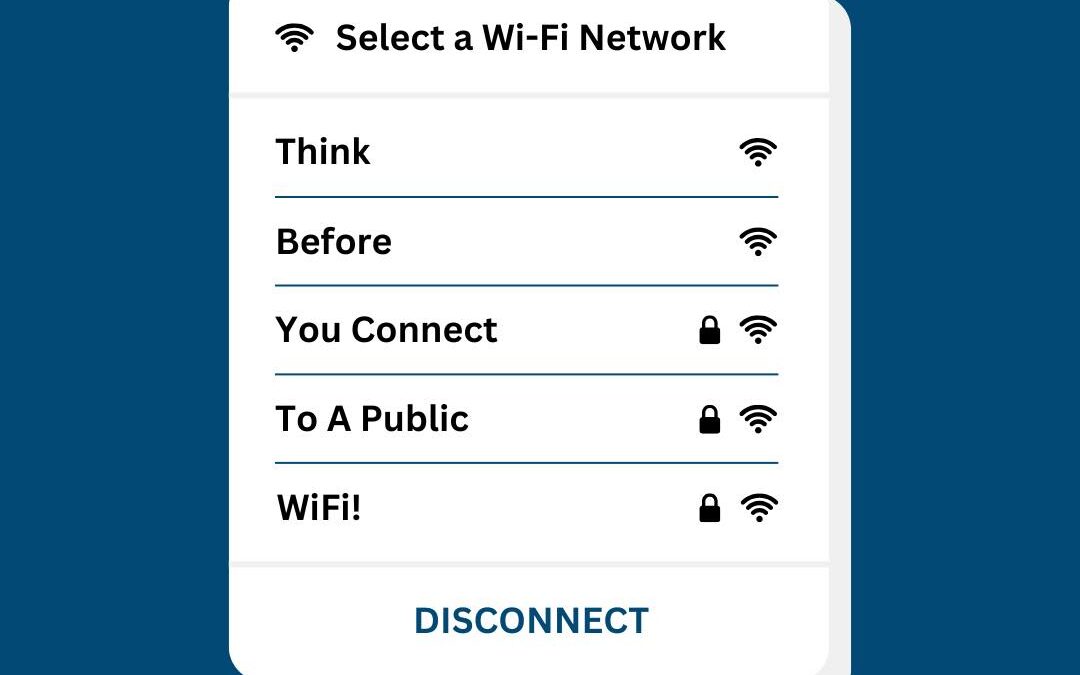
by PCS | Jan 26, 2025 | 2025, Tips & Tricks
Hackers can easily intercept your data on unsecured networks, putting your personal information, passwords, and banking details at risk. Stay Safe: Use a VPN to encrypt your connection. Avoid accessing sensitive accounts on public networks. Turn off automatic Wi-Fi...









