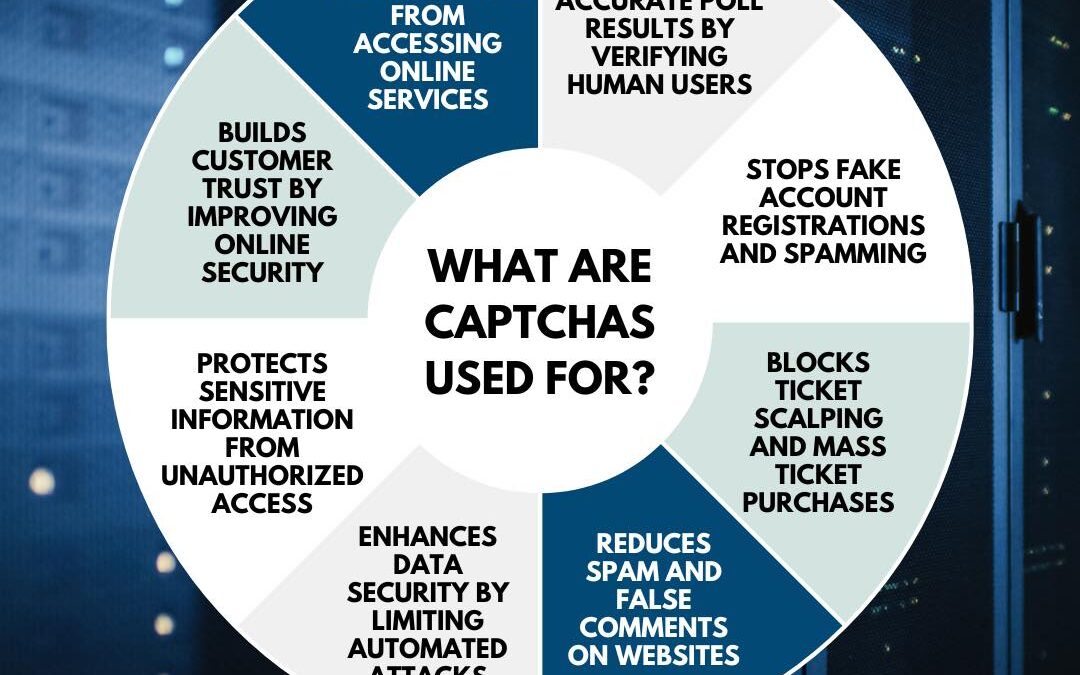
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
CAPTCHAs play a crucial role in maintaining online security by ensuring only humans can access specific online services. They help preserve the accuracy of online polls, limit fake account registrations, and prevent ticket scalping. CAPTCHAs also safeguard online...
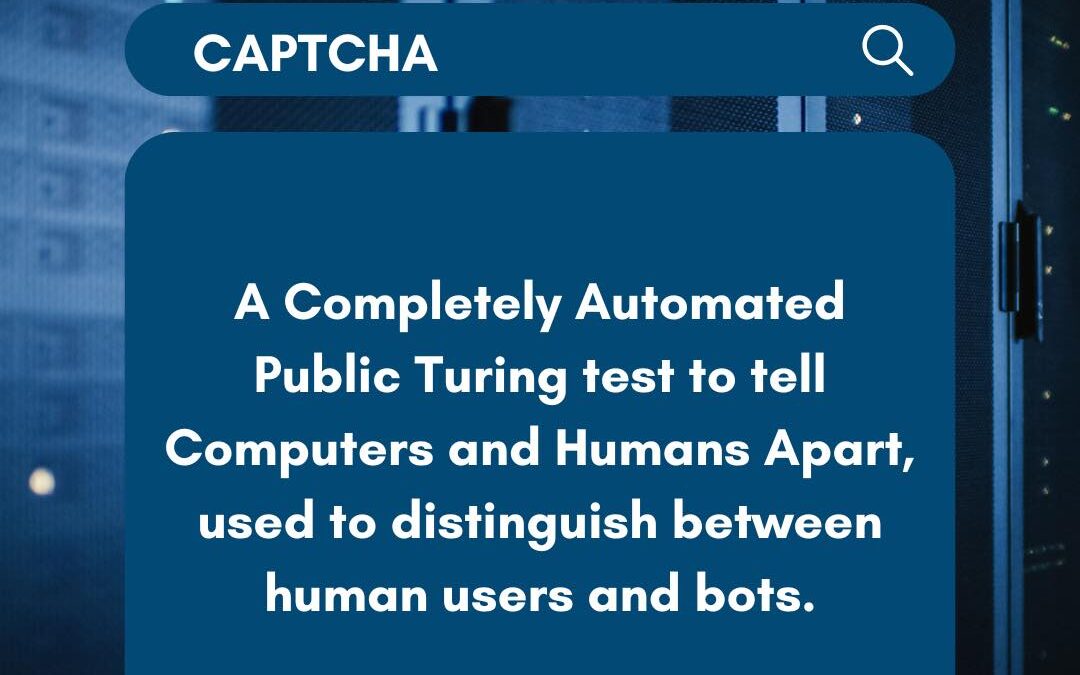
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
CAPTCHAs play a crucial role in cybersecurity by preventing automated bots from abusing websites or services. They present tasks that are simple for humans but challenging for bots, such as identifying distorted characters or selecting specific images. This ensures...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Cybersecurity services provide vital protection for businesses in today’s digital landscape. They shield sensitive data from breaches, ensuring that critical information remains secure and inaccessible to cybercriminals. With enhanced privacy measures, only authorized...

by PCS | Oct 12, 2024 | 2024, Tips & Tricks
In today’s fast-paced digital world, cybersecurity is a top priority for businesses of all sizes. The 5 C’s of Cybersecurity—Change, Compliance, Cost, Continuity, and Coverage—serve as a comprehensive guide for companies to protect their data and operations. From...

by PCS | Oct 12, 2024 | 2024, Tips & Tricks
A backdoor attack is like leaving a secret, unlocked door in your house that bypasses the front door security. Hackers exploit these hidden vulnerabilities to infiltrate systems undetected, allowing them to steal data, plant malware, or take control of networks. Even...









