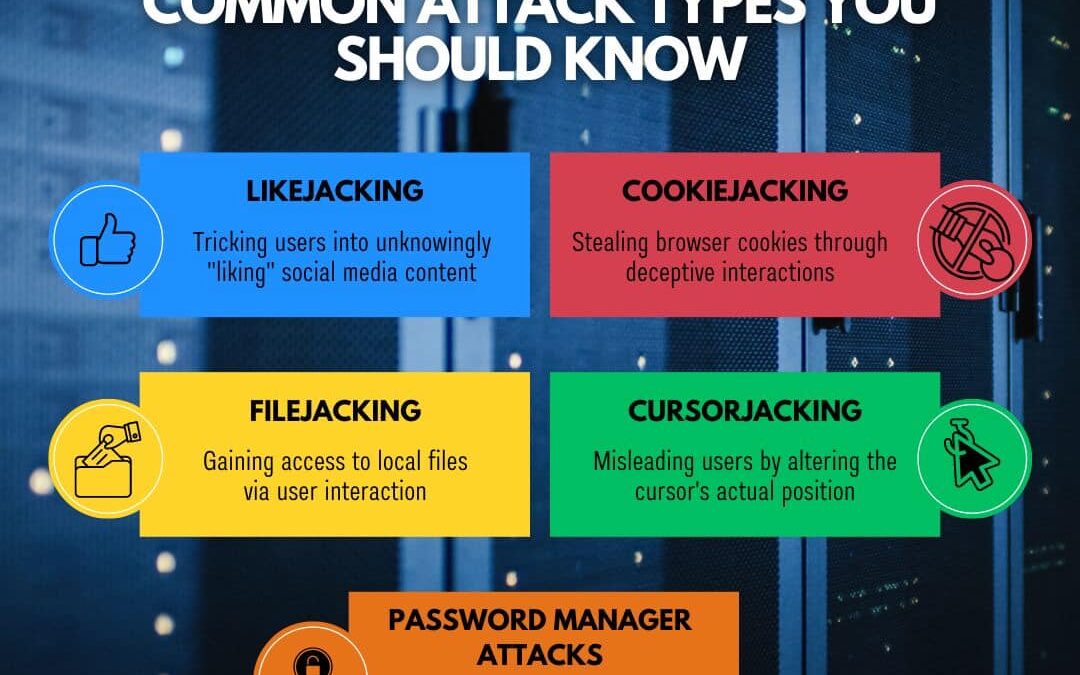
by PCS | Oct 12, 2024 | 2024, Tips & Tricks
Check out this infographic highlighting different types of clickjacking attacks—subtle yet dangerous methods used by cybercriminals to manipulate user actions. Understanding these tactics can help protect your data and online privacy. Don’t forget to stay...
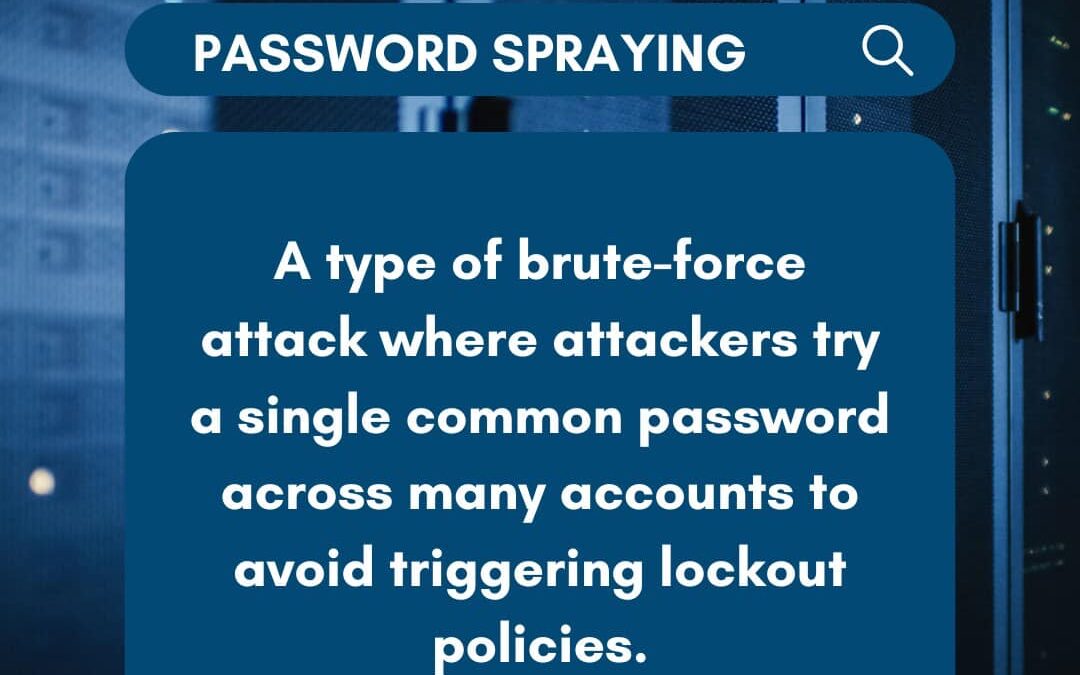
by PCS | Oct 12, 2024 | 2024, Tips & Tricks
Unlike traditional brute-force attacks, Password Spraying focuses on a low-effort, high-reward strategy. Attackers try a small set of commonly used passwords on a large number of accounts, often slipping under the radar of security policies that lock accounts after...
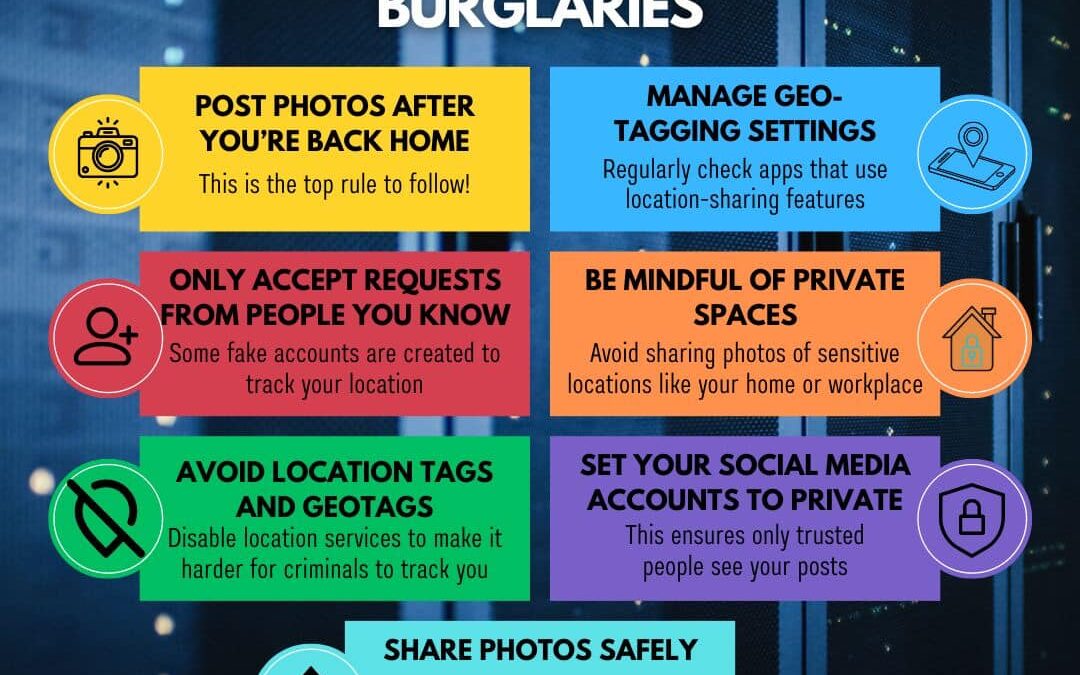
by PCS | Oct 12, 2024 | 2024, Tips & Tricks
Sharing your life online is fun, but it’s important to stay safe while doing it! Many don’t realize that oversharing can open doors for potential risks, including burglaries. Let’s all be mindful of how we use location-sharing features on social media. Small changes...

by PCS | Oct 12, 2024 | 2024, Tips & Tricks
This week’s cybersecurity term is “Salami Attack.” It’s a method of cybercrime where hackers steal tiny amounts from multiple accounts over time. These small, unnoticed thefts add up, creating significant financial damage. The subtlety of these attacks often makes...

by PCS | Oct 12, 2024 | 2024, Tips & Tricks
As the digital landscape evolves, so does the way our children communicate online. It’s crucial for parents to stay informed about the various acronyms and slang used across social media and messaging platforms. This infographic breaks down some of the most...









