by PCS | Oct 12, 2024 | 2024, Tips & Tricks
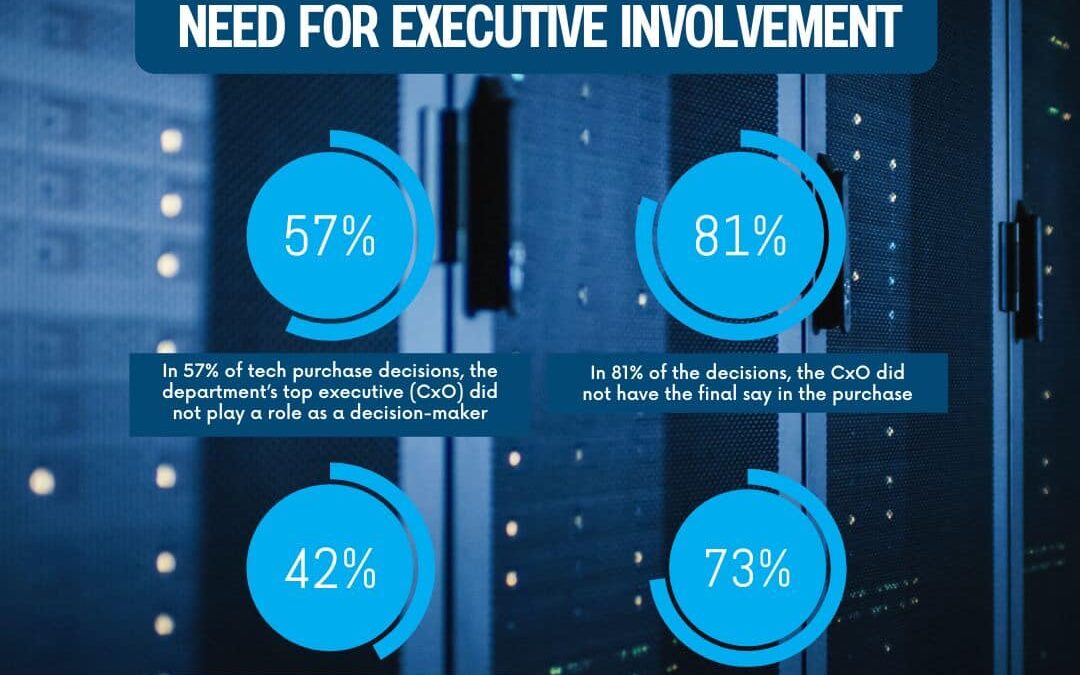
Executives often express dissatisfaction with technology implementations, primarily due to their limited involvement in the decision-making process. Greater engagement can ensure strategic alignment and optimize outcomes. By actively setting clear goals, reviewing...

by PCS | Oct 12, 2024 | 2024, Tips & Tricks
Our Cybersecurity Term of the Week is Daisy Chaining, a complex hacking method that can be hard to detect, as it relies on a series of smaller, interconnected vulnerabilities. Understanding this technique is crucial for improving your organization’s defense...

by PCS | Oct 12, 2024 | 2024, Tips & Tricks
This infographic highlights the key attributes that every successful CISO needs: executive presence, business knowledge, and technical acumen. These qualities enable them to bridge the gap between security and business operations, ensuring a secure and resilient...

by PCS | Oct 12, 2024 | 2024, Updates
We are happy to be back at PDSC and work with their leaders to build a culture of security, one step at a time. Just because… Security Awareness is for Everyone (Just be SAFE) is our primary program that aims to help organzations realize that security is not...

by PCS | Oct 12, 2024 | 2024, Tips & Tricks
Footprinting is a crucial first step in the world of cybersecurity, where attackers or security professionals gather information about a target system. By using various tools and techniques, they can uncover valuable data such as network structures, IP addresses, or...









