by PCS | Oct 12, 2024 | 2024, Tips & Tricks
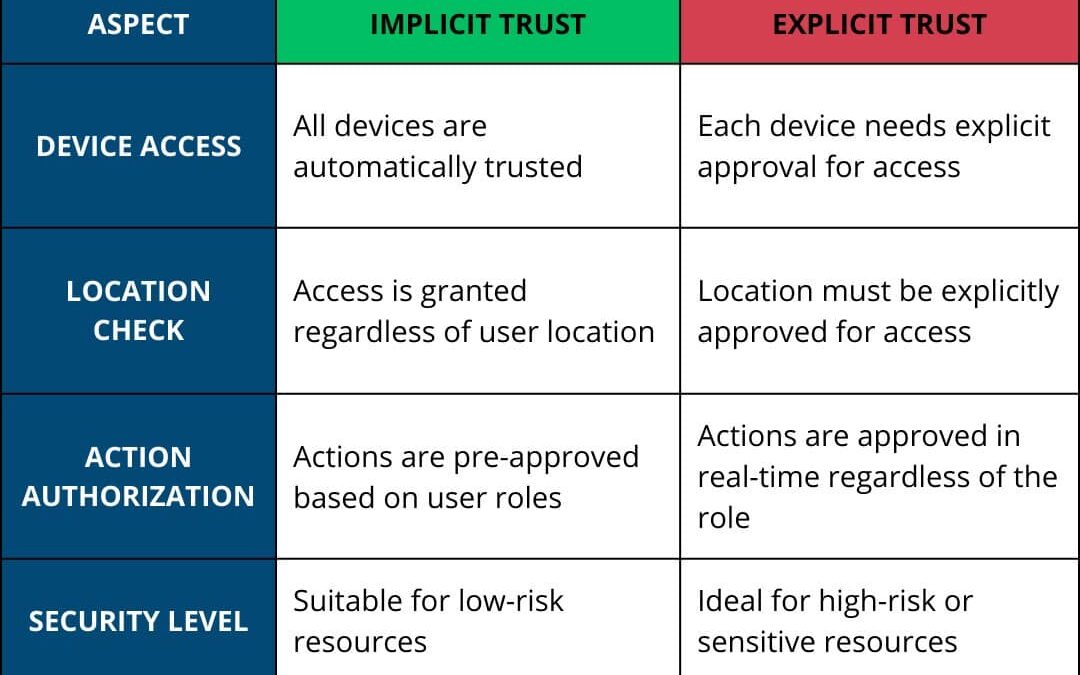
In access management, implicit trust operates under the assumption that everyone in the system is trustworthy, allowing unrestricted access until proven otherwise. In contrast, explicit trust requires continuous verification, demanding users to prove their identity...
by PCS | Oct 12, 2024 | 2024, Tips & Tricks
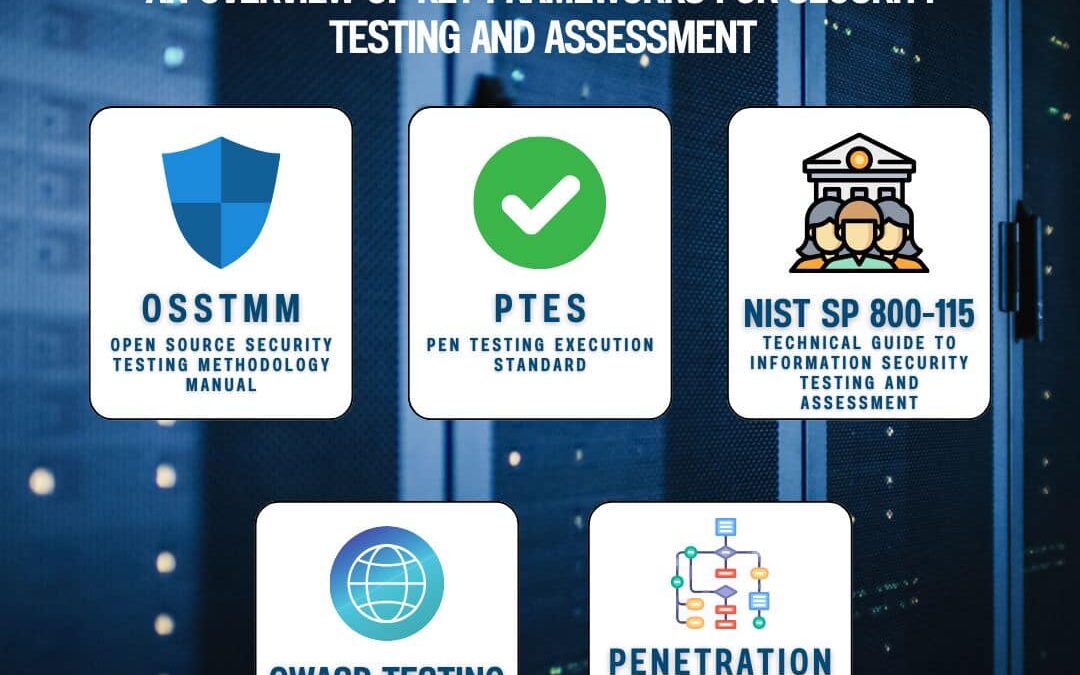
Vulnerability Assessment and Penetration Testing (VAPT) frameworks provide structured approaches to identifying and addressing security vulnerabilities. Here’s a quick overview of five key frameworks that guide the security testing process: OSSTMM (Open Source...

by PCS | Oct 12, 2024 | 2024, Tips & Tricks
This week’s cybersecurity term is Shift Left Security! In traditional development, security testing often happens after the software is built, leading to potential delays or costly fixes. However, by shifting left, security considerations are integrated from the very...
by PCS | Oct 12, 2024 | 2024, 2024, Tips & Tricks, Updates
Thank you Philippine SME Business Network for inviting Pineda Cybersecurity to be part of the #PhilSME Business Show. The interview starts at 26:00. #pinedacybersecurity #cybersecuritymakessensehere...

by PCS | Oct 12, 2024 | 2024, Tips & Tricks
Penetration testing comes in different forms, each with varying levels of knowledge provided to the tester. From the limited knowledge in Black Box to the complete transparency of White Box, these tests help organizations uncover vulnerabilities and strengthen their...








