
by PCS | Oct 12, 2024 | 2024, Tips & Tricks
This week’s cybersecurity term is Threat Modeling, a proactive approach to identifying and mitigating potential security issues before deployment, helping to reduce the attack surface. Key techniques include: STRIDE: Focuses on identifying six key threat...
by PCS | Oct 12, 2024 | 2024, Tips & Tricks
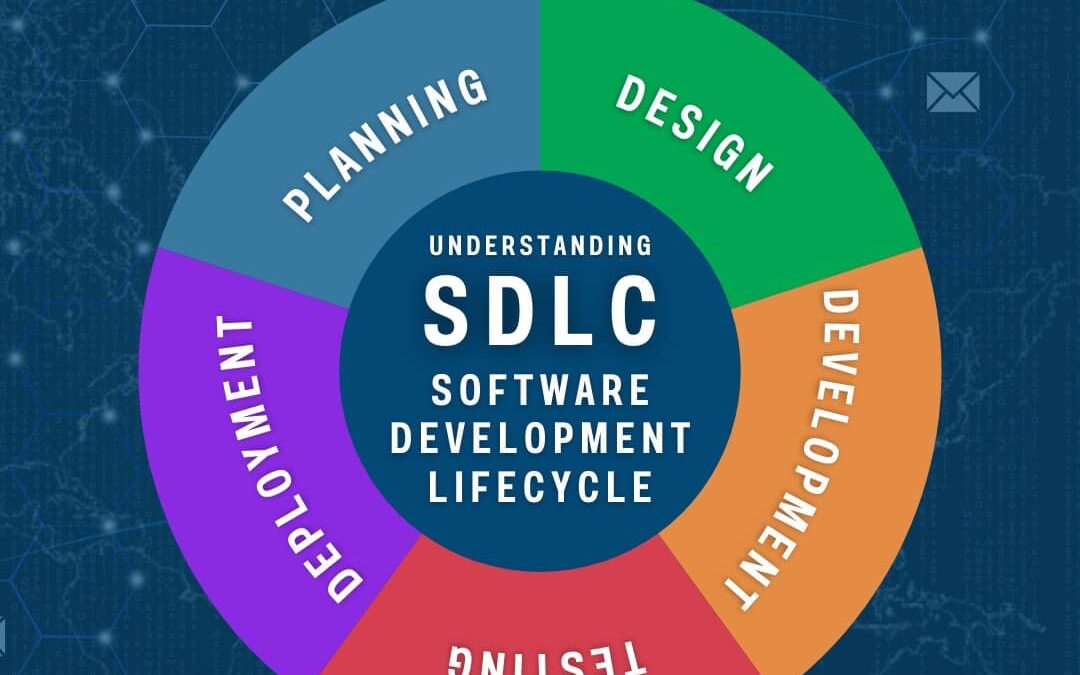
Understanding the Software Development Lifecycle (SDLC) is crucial for integrating security at every stage. Planning: Define scope, objectives, and security requirements. Design: Incorporate security into architecture and design. Development: Implement secure coding...

by PCS | Sep 5, 2024 | 2024, 2024, Tips & Tricks, Updates
Tracking security metrics helps ensure that your cybersecurity efforts are effective and continuously improving. It’s crucial to keep leadership updated with clear reports, so everyone is aligned on progress and potential risks. Metrics like vulnerability count,...

by PCS | Sep 5, 2024 | 2024, Updates
Our Cybersecurity Term of the Week is Brute Force Attacks, which remain as one of the most persistent and straightforward methods used by cybercriminals to gain unauthorized access to systems By repeatedly trying different password combinations, attackers can break...
by PCS | Sep 5, 2024 | 2024, Updates
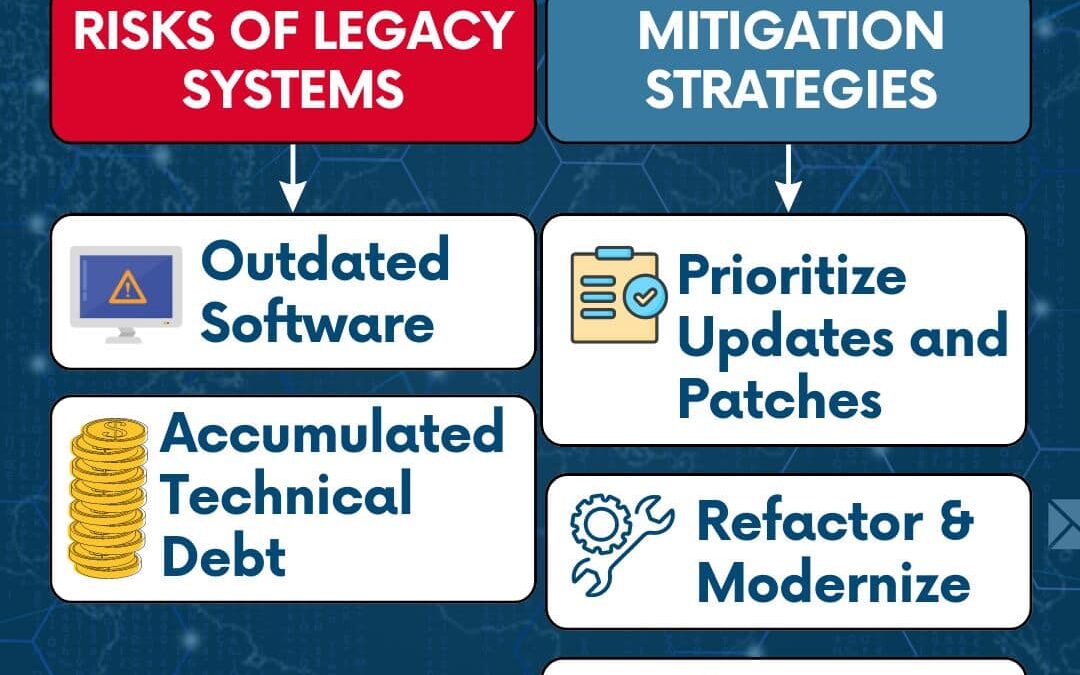
Dealing with legacy systems and technical debt is crucial for maintaining the security and efficiency of your business. Prioritizing updates and patches for critical systems helps safeguard your operations, while refactoring and modernizing legacy code ensures...









