
by PCS | Aug 30, 2024 | 2024, 2024, Tips & Tricks, Updates
Threat modeling takes an attacker’s perspective to identify vulnerabilities in your environment, system, or application. STRIDE, a popular threat model, categorizes security threats into six key areas: Spoofing:Impersonating someone or something...
by PCS | Aug 30, 2024 | 2024, 2024, Tips & Tricks, Updates
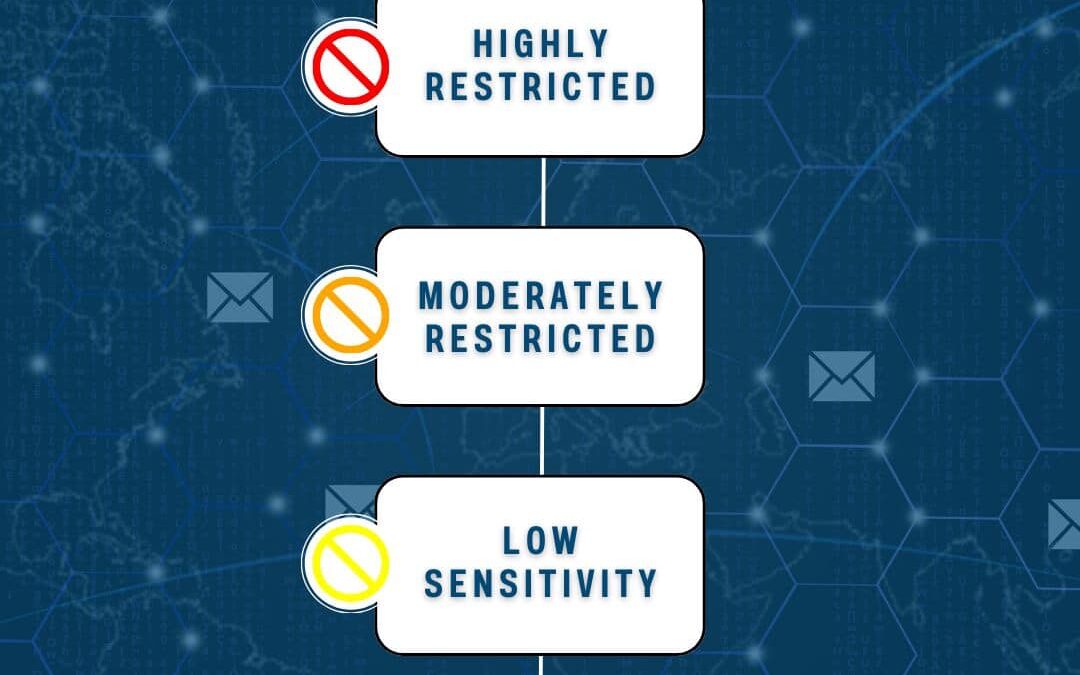
Understanding Data Sensitivity Levels is crucial for effective asset security management. This flowchart breaks down the different levels, and explains their potential impacts.Highly Restricted:Compromise could risk the organization’s future, cause substantial...

by PCS | Aug 30, 2024 | 2024, 2024, Tips & Tricks, Updates
This review outlines the six fundamental principles established in Article 5 of the GDPR, guiding the use of personal data: Lawfulness,Fairness,and Transparency:Data must be collected, processed, used, shared, stored, and destroyed in a manner that is legal, fair,...
by PCS | Aug 30, 2024 | 2024, 2024, Tips & Tricks, Updates
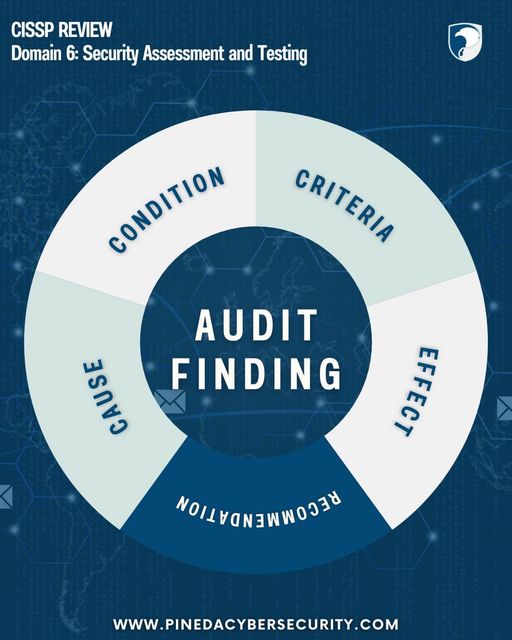
Understanding the core elements of an audit is crucial for effective security assessment and testing. This diagram breaks down the key components of a finding: Condition:A description of the audit’s findings.Criteria:The benchmarks used to evaluate the...
by PCS | Aug 30, 2024 | 2024, 2024, Tips & Tricks, Updates
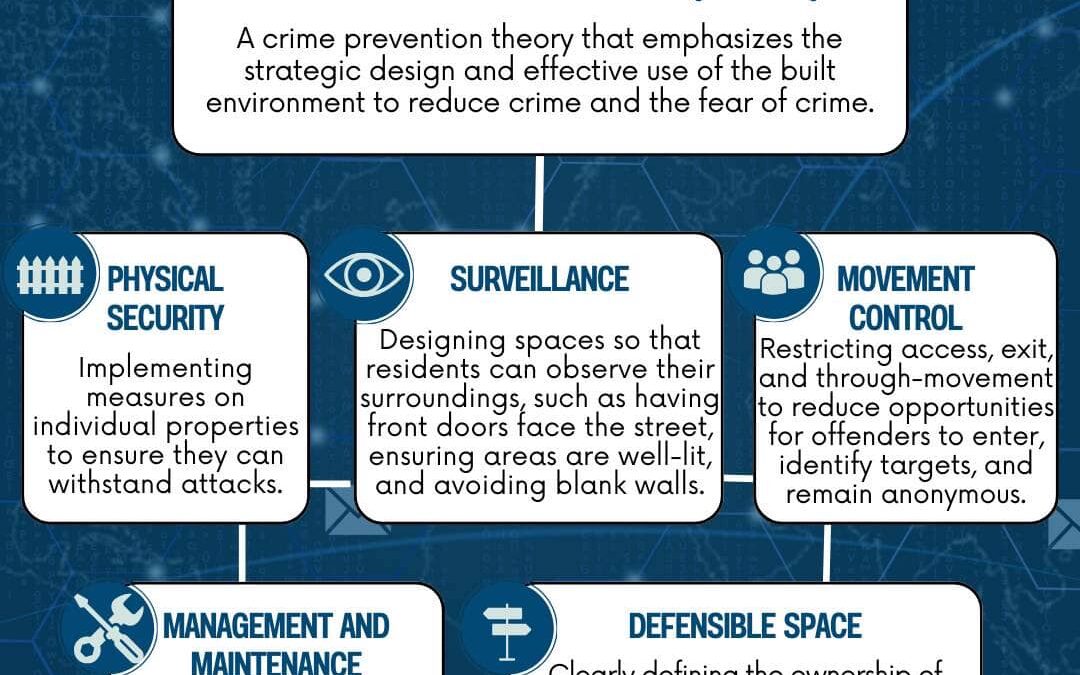
Here’s how CPTED can transform our communities. By integrating strategic design and effective use of our environments, we can significantly reduce crime and enhance safety. This theory offers practical insights to make our neighborhoods more secure and welcoming. In...









