by PCS | Dec 19, 2024 | 2024, Tips & Tricks
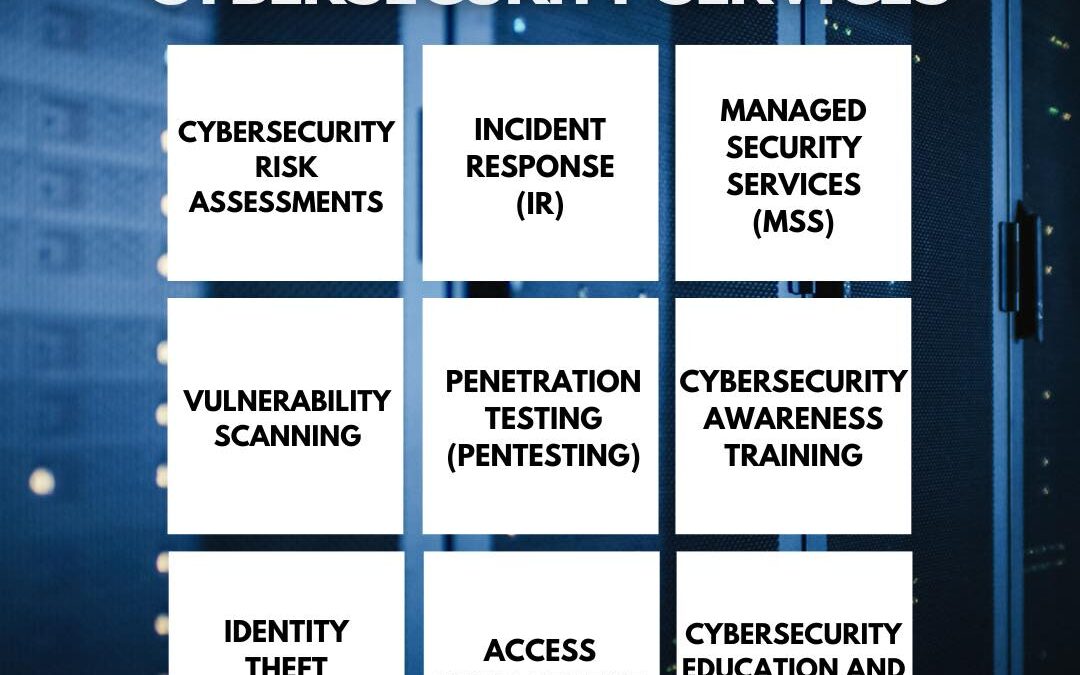
Cybersecurity services are essential for protecting data, systems, and networks from various threats. This infographic highlights the nine key types of cybersecurity services that organizations can implement to safeguard their assets. From risk assessments and...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
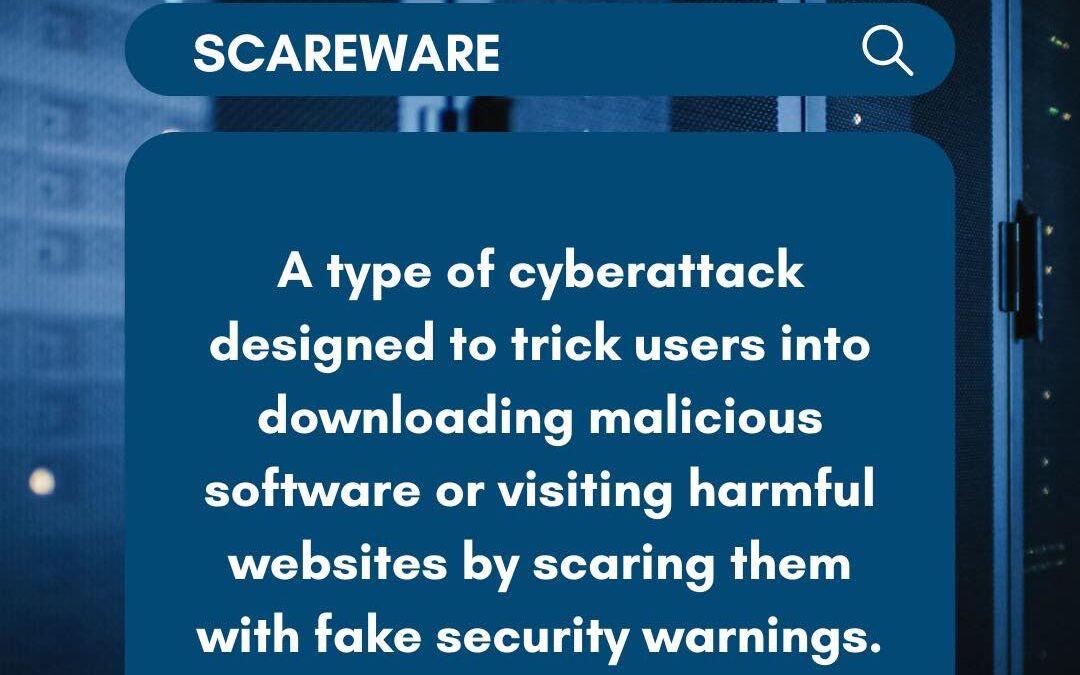
Ever seen a sudden pop-up claiming your computer is infected? That’s classic scareware in action! By preying on your fear, these cybercriminals push you to download “solutions” that are actually harmful malware. The goal is to steal personal data or convince you to...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
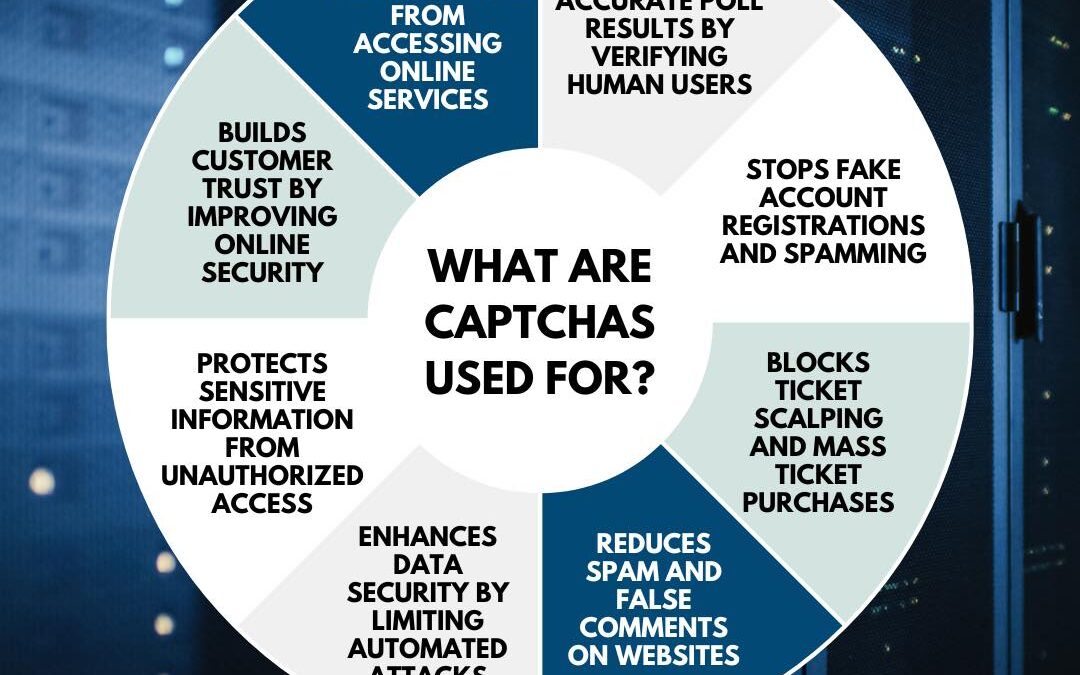
CAPTCHAs play a crucial role in maintaining online security by ensuring only humans can access specific online services. They help preserve the accuracy of online polls, limit fake account registrations, and prevent ticket scalping. CAPTCHAs also safeguard online...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
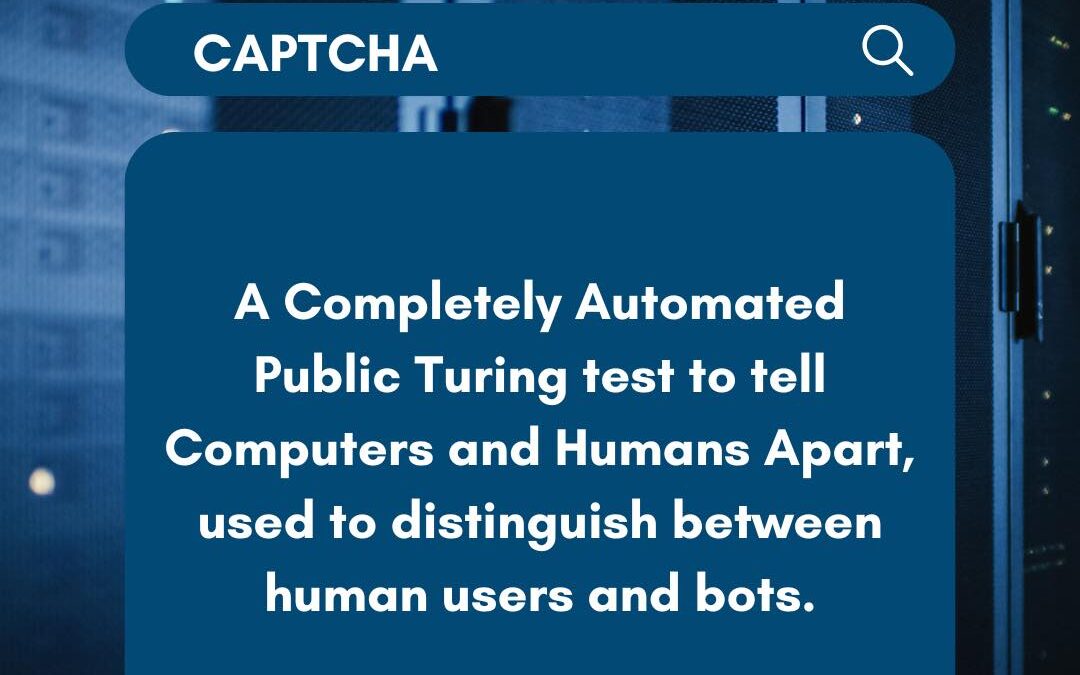
CAPTCHAs play a crucial role in cybersecurity by preventing automated bots from abusing websites or services. They present tasks that are simple for humans but challenging for bots, such as identifying distorted characters or selecting specific images. This ensures...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Cybersecurity services provide vital protection for businesses in today’s digital landscape. They shield sensitive data from breaches, ensuring that critical information remains secure and inaccessible to cybercriminals. With enhanced privacy measures, only authorized...









