
by PCS | Sep 5, 2024 | 2024, 2024, Tips & Tricks, Updates
Tracking security metrics helps ensure that your cybersecurity efforts are effective and continuously improving. It’s crucial to keep leadership updated with clear reports, so everyone is aligned on progress and potential risks. Metrics like vulnerability count,...
by PCS | Sep 5, 2024 | 2024, 2024, Tips & Tricks, Updates
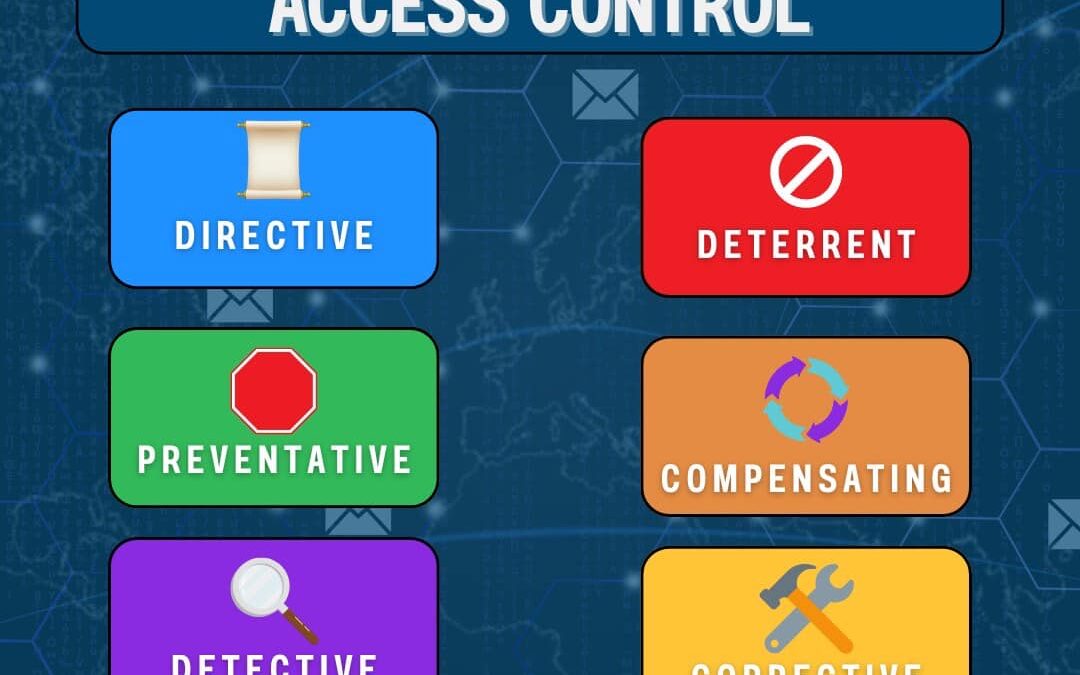
Understanding the different categories of access control is crucial for effective security management. Here are the key categories: Directive: Specify rules of behavior. Deterrent: Discourage people, change behavior. Preventative: Prevent incidents or breaches....
by PCS | Sep 5, 2024 | 2024, 2024, Tips & Tricks, Updates
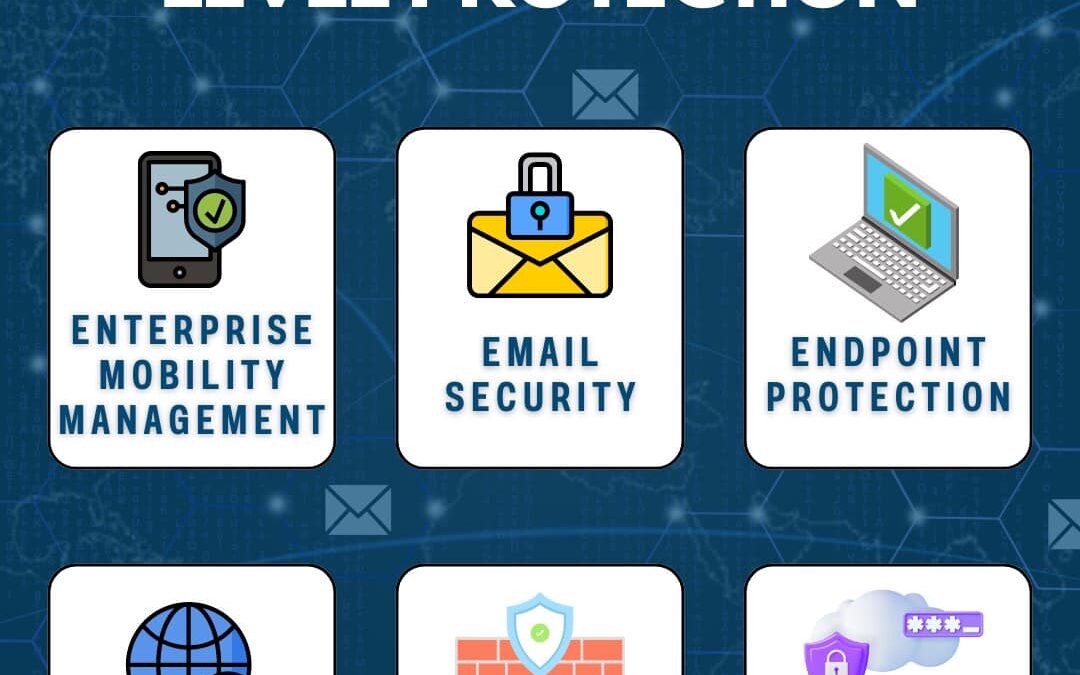
In today’s digital world, mobile devices are integral to business operations, but they also introduce unique security challenges. To ensure robust mobile security, here are the key areas to focus on: Enterprise Mobility Management (EMM): Manage and secure...

by PCS | Sep 5, 2024 | 2024, 2024, Tips & Tricks, Updates
Data remanence refers to the leftover data that persists even after deletion, posing a significant security risk. To effectively mitigate the threat of unauthorized data recovery, it’s crucial to address this issue properly. Among the methods to deal with data...

by PCS | Sep 5, 2024 | 2024, 2024, Tips & Tricks, Updates
A strong Risk Management Strategy is essential to achieving the goals of any organization’s risk management objectives. The primary goals are to recognize all possible risks and reduce them to an acceptable level, ensuring the organization remains secure and...
by PCS | Sep 5, 2024 | 2024, 2024, Tips & Tricks, Updates
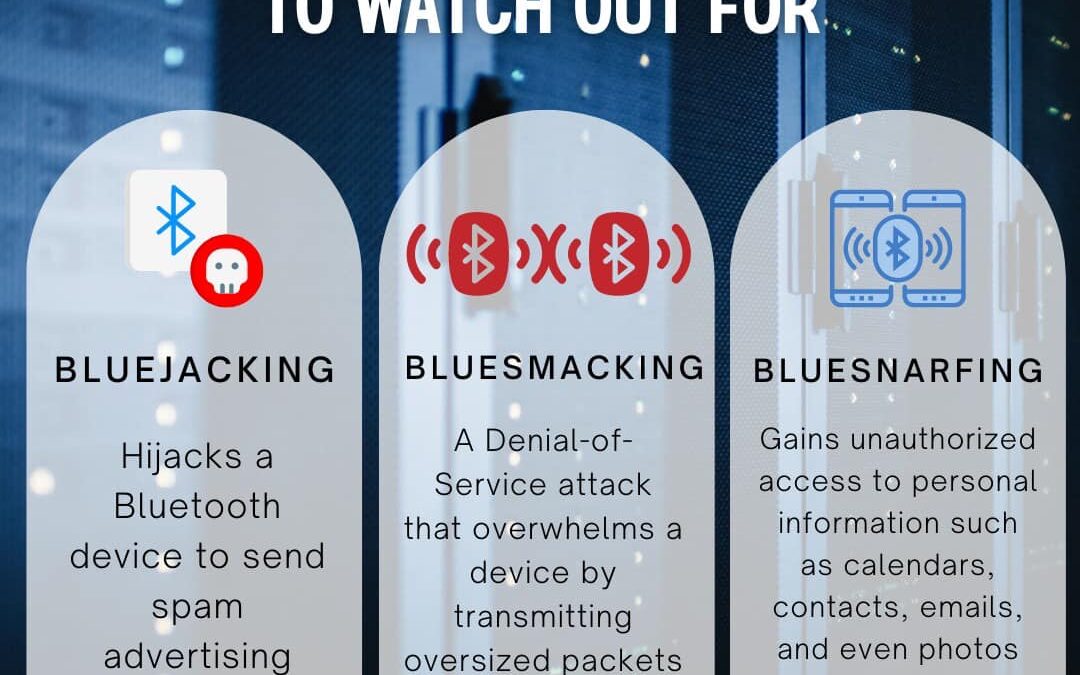
Bluetooth technology offers incredible convenience, allowing seamless connectivity between devices, but it also comes with certain risks. This convenience can expose your devices to various security threats. Here are some of the most common Bluetooth attacks. Stay...










