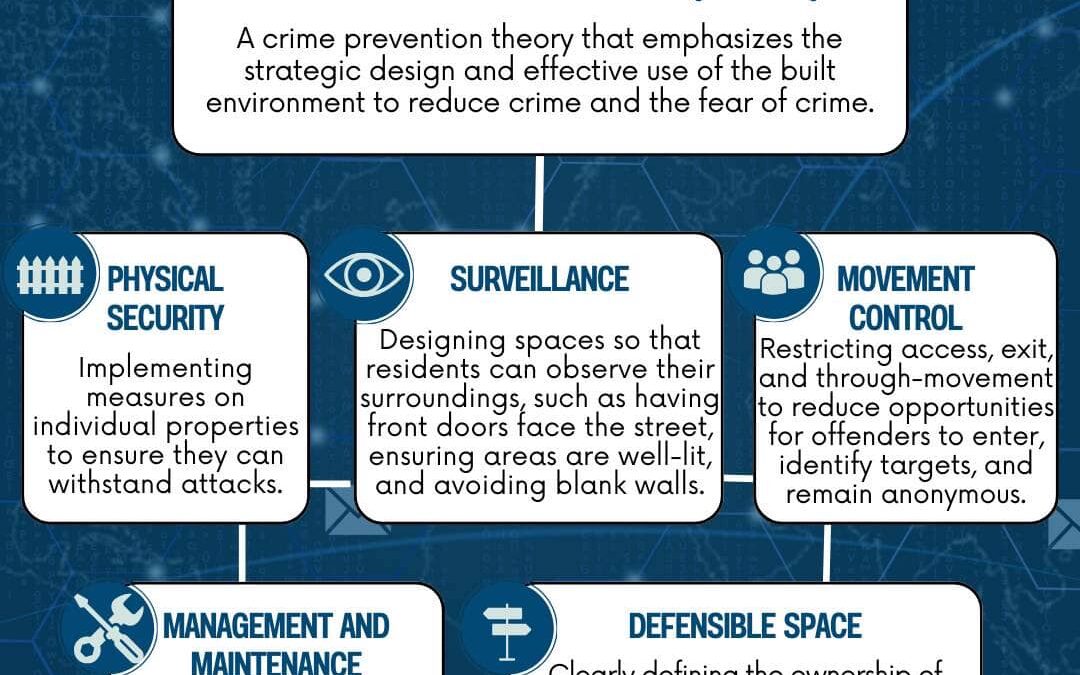
by PCS | Aug 30, 2024 | 2024, 2024, Tips & Tricks, Updates
Here’s how CPTED can transform our communities. By integrating strategic design and effective use of our environments, we can significantly reduce crime and enhance safety. This theory offers practical insights to make our neighborhoods more secure and welcoming. In...

by PCS | Aug 30, 2024 | 2024, 2024, Tips & Tricks, Updates
Introducing the ISC2 Code of Ethics – a cornerstone for all CISSP professionals. These guiding principles ensure integrity, competence, and public trust within the cybersecurity community. Here’s an essential review to reinforce your commitment to ethical practices in...
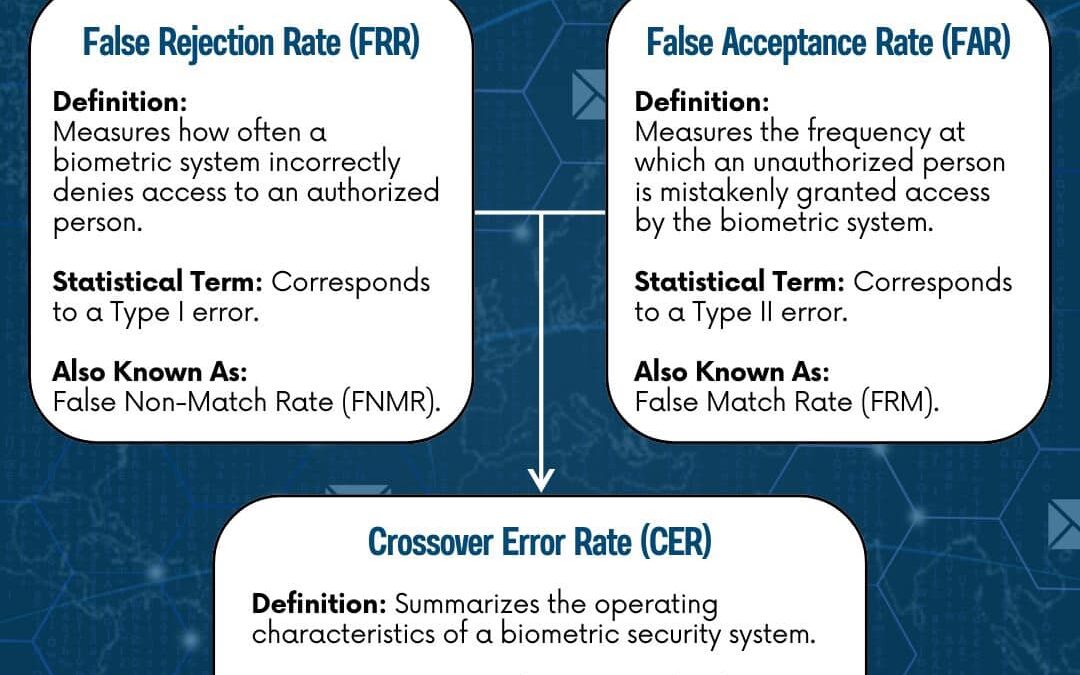
by PCS | Aug 30, 2024 | 2024, 2024, Tips & Tricks, Updates
Understanding biometric security is crucial for any cybersecurity professional. Today, let’s look into the key concepts of False Acceptance Rate (FAR), False Rejection Rate (FRR), and Crossover Error Rate (CER). #PinedaCyberSecurity #CyberSecurityMakesSenseHere...

by PCS | Aug 30, 2024 | 2024, Tips & Tricks
Understanding Identity Assurance Levels (IAL) is crucial for anyone diving into cybersecurity. IAL measures the confidence a system has in a user’s identity via three levels, each represents a different degree of security. Swipe through the slides for more...

by PCS | Aug 30, 2024 | 2024, Tips & Tricks
Attention all cybersecurity professionals! When performing penetration testing, it’s crucial to adhere to ethical guidelines to protect customer data and maintain trust. Your integrity ensures not only the safety of your clients but also upholds the reputation...

by PCS | Aug 30, 2024 | 2024, Tips & Tricks
Protecting customer data in Health Maintenance Organizations (HMOs) is essential to maintain trust and ensure legal compliance. Learn about PHI and key data protection measures, swipe through the slides for more information. #PinedaCyberSecurity...










