
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
In today’s fast-evolving digital landscape, threat analysis is your shield against unforeseen cyber-attacks. By assessing vulnerabilities and studying exploitation tactics in real time, organizations can strengthen their defenses and stay ahead of sophisticated...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
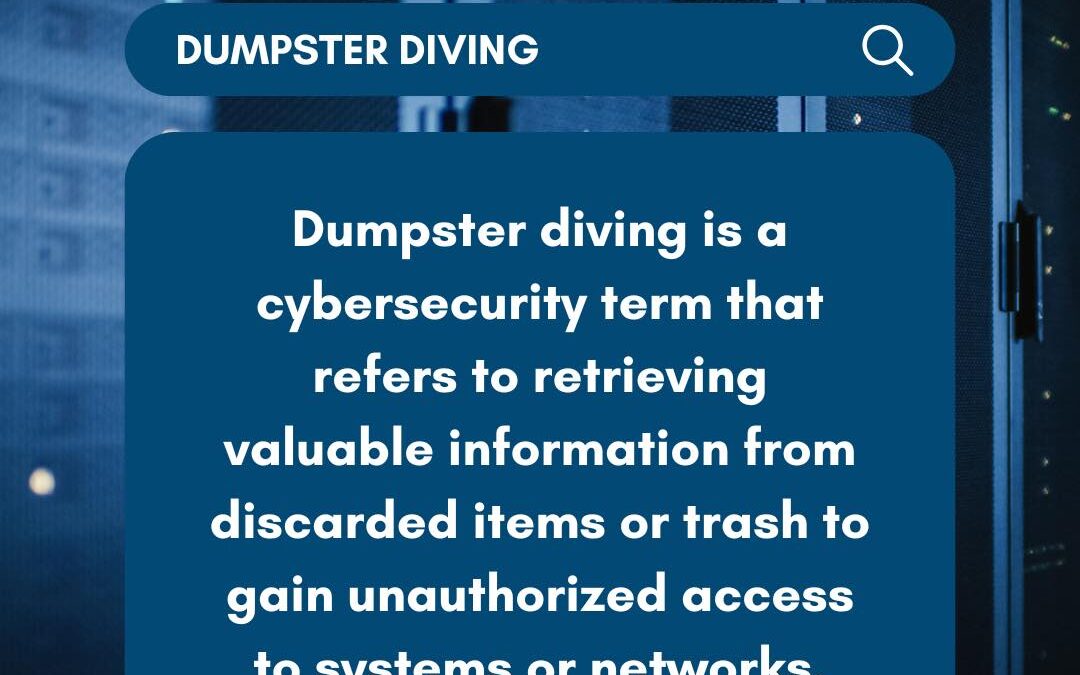
Cybersecurity threats can come from unexpected places—including the trash! Dumpster diving is a technique where attackers sift through discarded items looking for sensitive information. Even seemingly harmless materials like phone directories, old documents, or...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
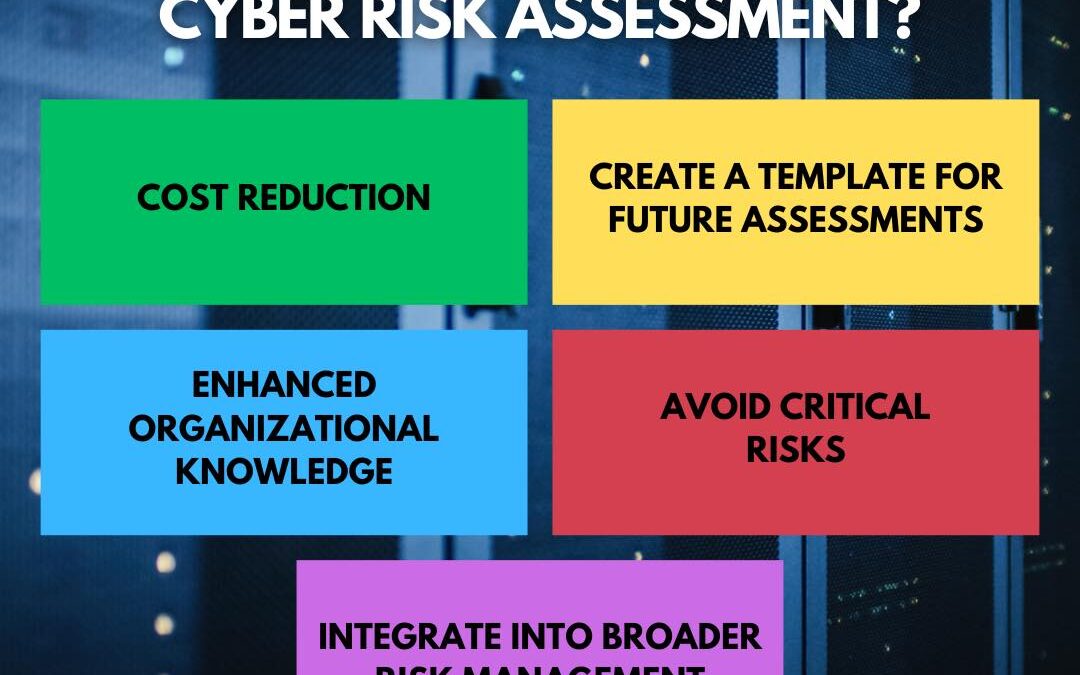
Performing a cyber risk assessment helps your organization in multiple ways. Reduce costs by identifying and mitigating risks early, create repeatable processes for future assessments, and enhance your knowledge of vulnerabilities. Avoid data breaches, regulatory...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
As organizations move to the cloud, security becomes paramount. Protecting sensitive information in cloud environments requires a robust approach to prevent data breaches and unauthorized access. From encryption to access control, effective cloud security safeguards...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Attention Parents! Scammers are targeting Aussie kids on social media with fake profiles and websites that look like trusted brands. In 2024 alone, over $129,700 has been lost to these scams, with children and teens falling victim to online fraud. Stay vigilant and...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
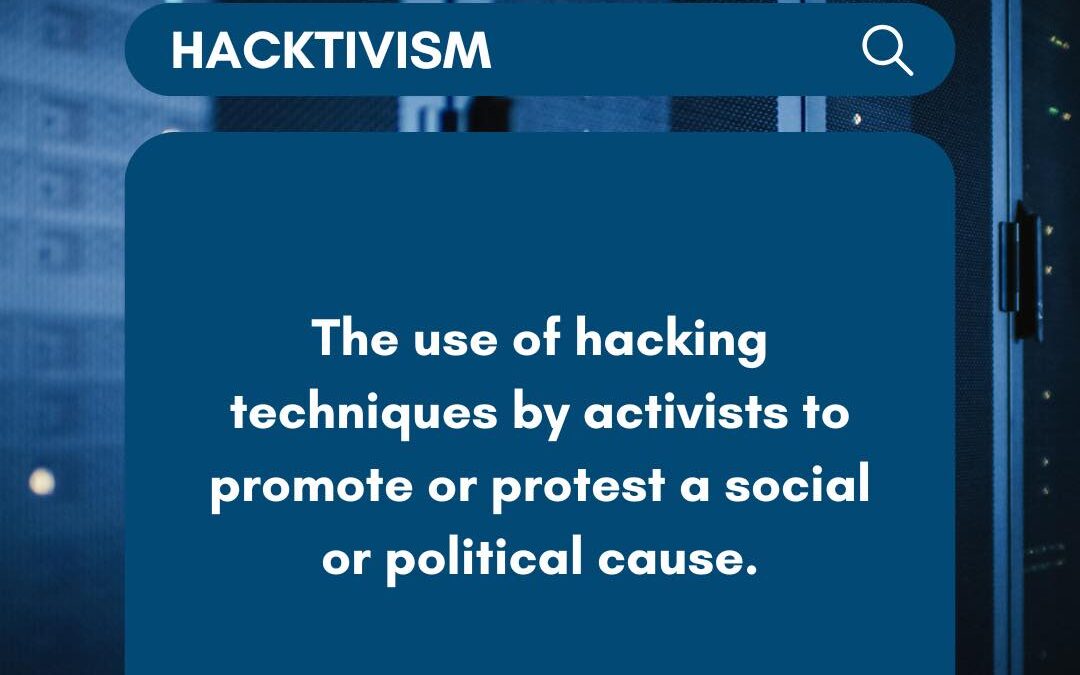
Hacktivism represents a fusion of digital skills and activism, where individuals or groups leverage hacking to champion social or political causes. Their targets often include governments, corporations, or other significant institutions they perceive as unjust or...










