by PCS | Dec 19, 2024 | 2024, Tips & Tricks
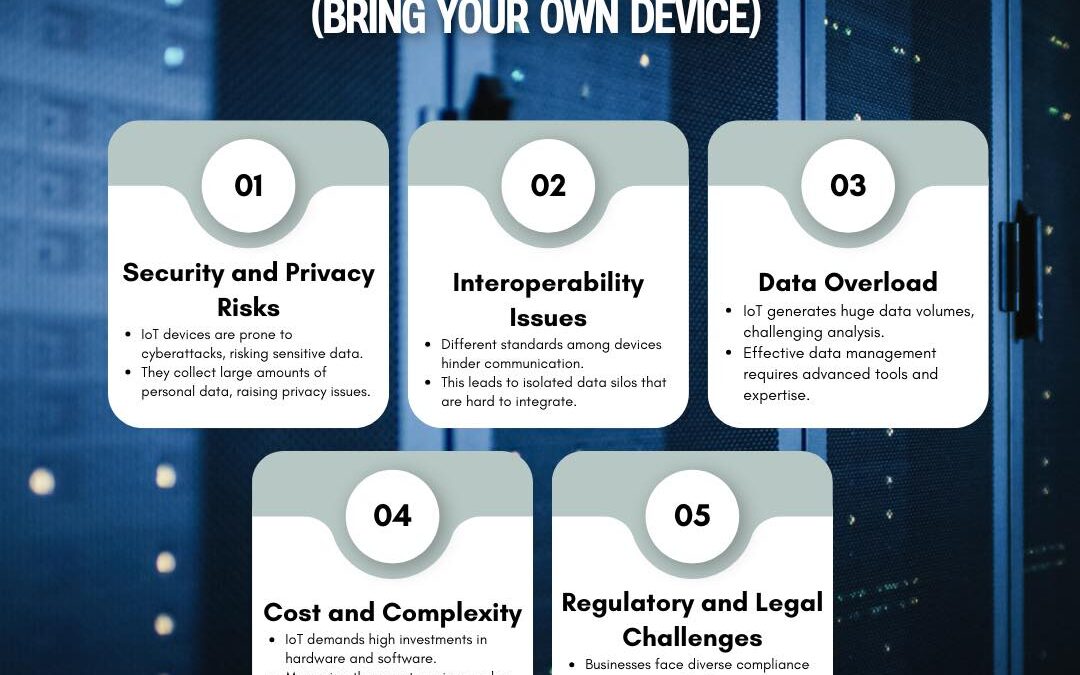
The Internet of Things (IoT) is transforming industries and daily life, but it also brings unique risks and challenges that demand attention. From security vulnerabilities and data overload to regulatory concerns, businesses need to navigate these complexities to...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
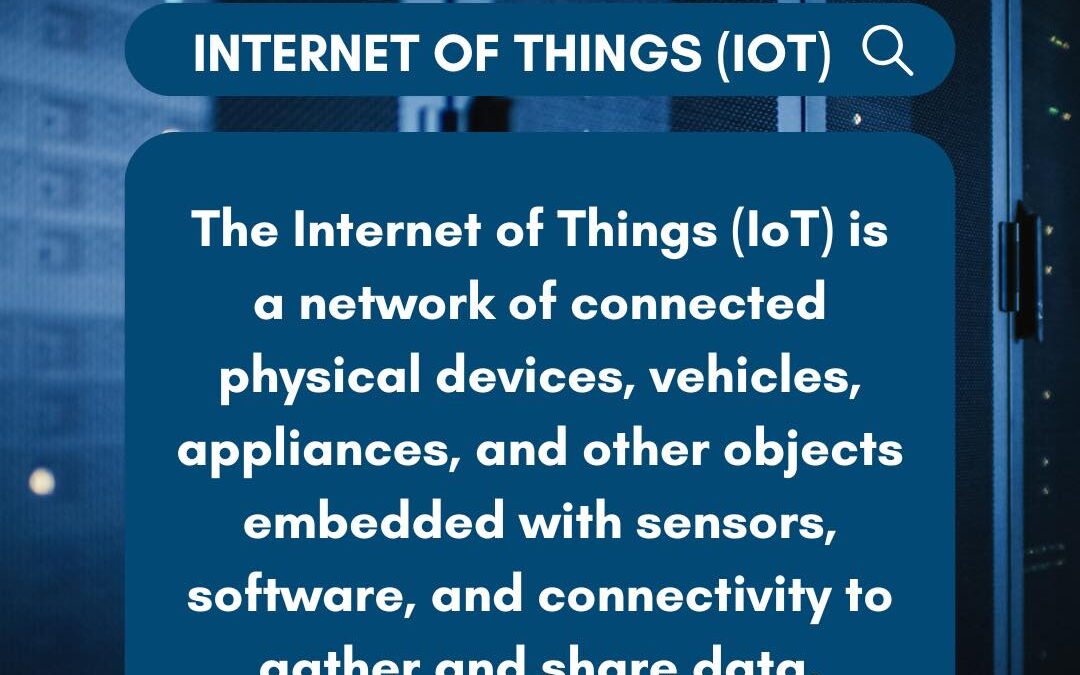
Imagine a world where devices—from home appliances to industrial machines—are constantly communicating, sharing real-time data, and automating tasks. IoT brings this to life, creating an interconnected network that improves efficiency, convenience, and insights across...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
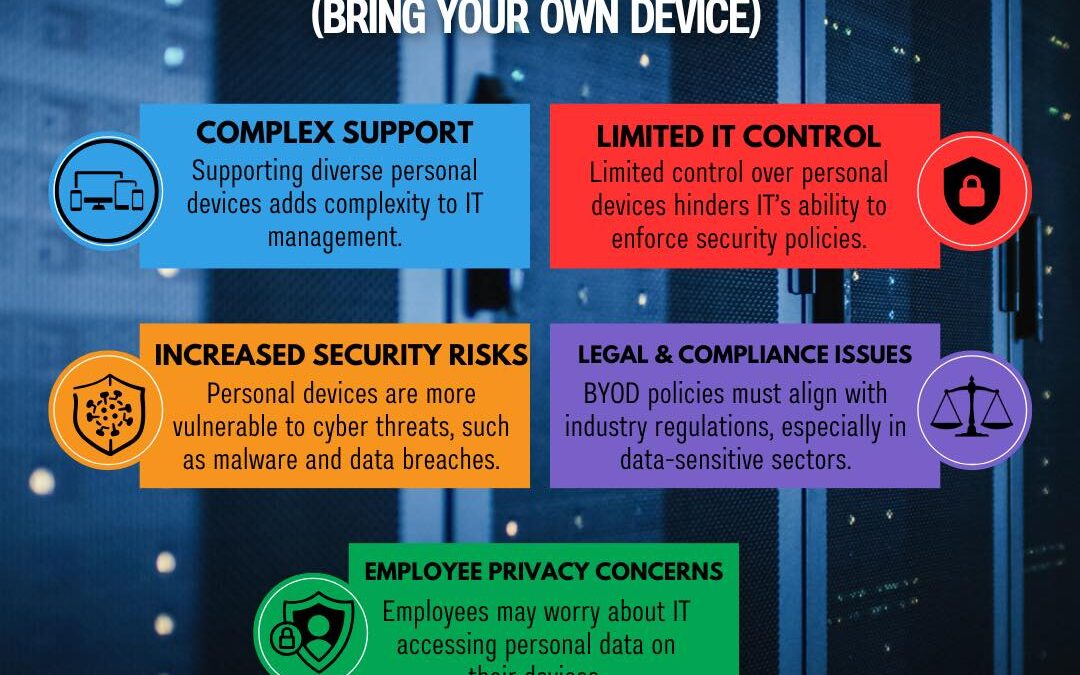
Bring Your Own Device (BYOD) policies offer many benefits, but they also introduce specific challenges that organizations must navigate carefully. From complex IT support to increased security risks, each aspect of BYOD presents unique issues that require thoughtful...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
The Bring Your Own Device (BYOD) policy has evolved to accommodate today’s flexible work environments, particularly with the shift to remote and hybrid work. Originally focusing on smartphones, BYOD policies now cover various devices as employees increasingly use...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
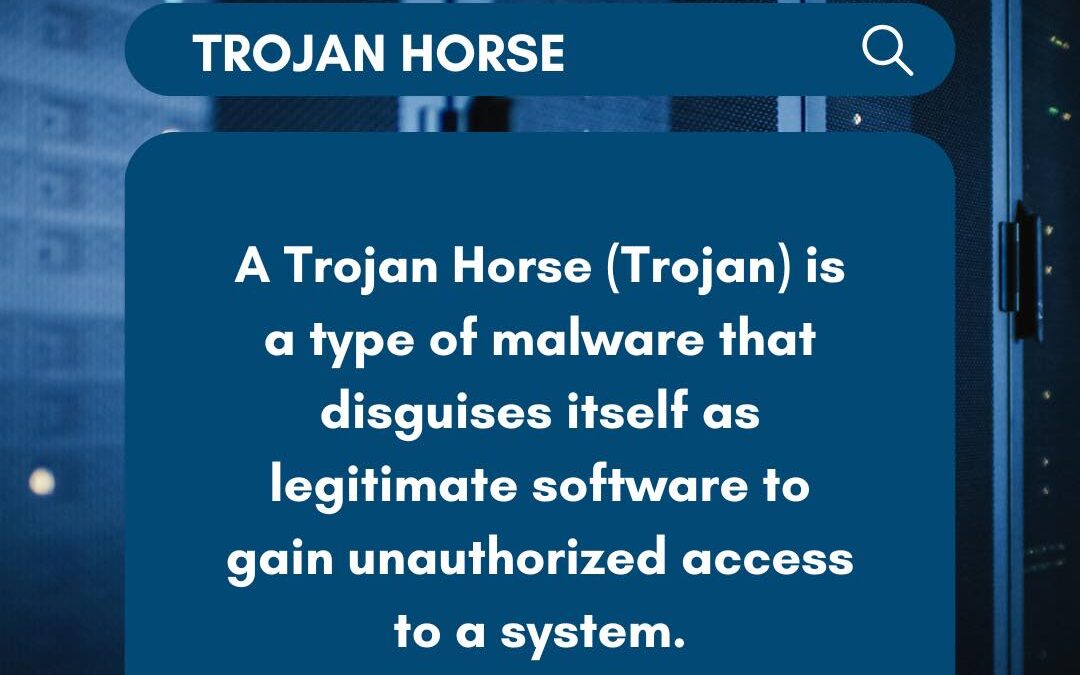
A Trojan Horse is a classic tool in a hacker’s arsenal, slipping past defenses by pretending to be trusted software. Once inside, it can wreak havoc—exporting data, altering files, or even deleting crucial information. Trojans often find their way in through enticing...
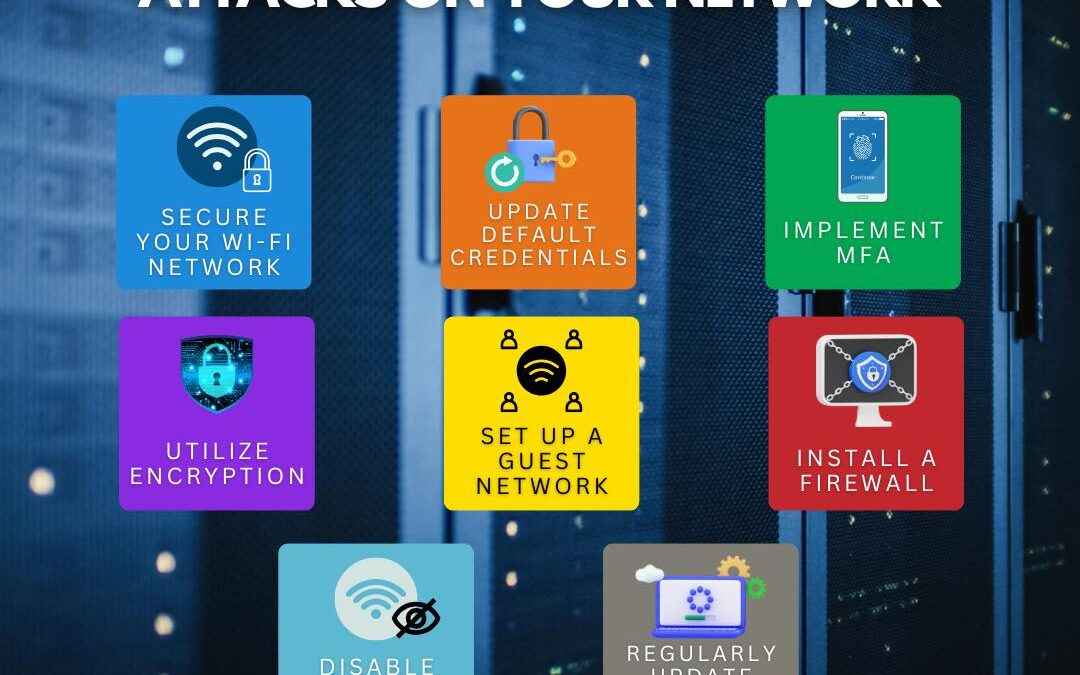
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Protecting your network from wardriving attacks starts with simple, proactive steps. By securing your Wi-Fi, updating credentials, and utilizing encryption, you can significantly reduce the risk of unauthorized access. Setting up a guest network, enabling multi-factor...










