
by PCS | Oct 12, 2024 | 2024, Tips & Tricks
Imagine millions of infected devices silently working together, all under the control of one attacker—that’s a botnet. These devices, or “bots,” can be manipulated remotely to launch massive attacks, steal data, or send spam, with the bot-herder...
by PCS | Oct 12, 2024 | 2024, Tips & Tricks
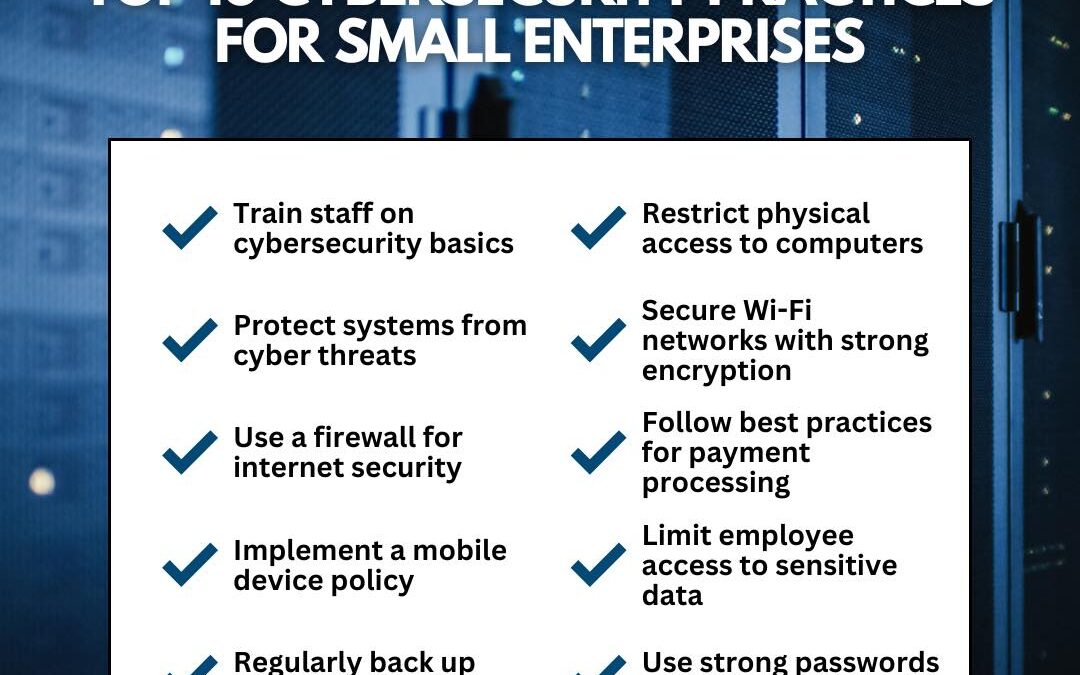
Implementing robust cybersecurity measures is crucial for small businesses in today’s digital landscape. From employee training to securing your Wi-Fi networks and enforcing strong password protocols, these essential tips can help safeguard your data and protect...

by PCS | Oct 12, 2024 | 2024, Tips & Tricks
Honeypots are a clever form of cybersecurity defense, designed to look like legitimate digital assets, such as servers or applications, to trick attackers into targeting a decoy. Once an adversary interacts with the honeypot, cybersecurity teams can observe their...

by PCS | Oct 12, 2024 | 2024, Tips & Tricks
Cryptojacking is a sneaky cybercrime where hackers hijack your device’s processing power to mine cryptocurrency for their gain, all without your consent. This malicious software often remains hidden, silently draining your system’s resources, slowing down performance,...
by PCS | Oct 12, 2024 | 2024, Tips & Tricks
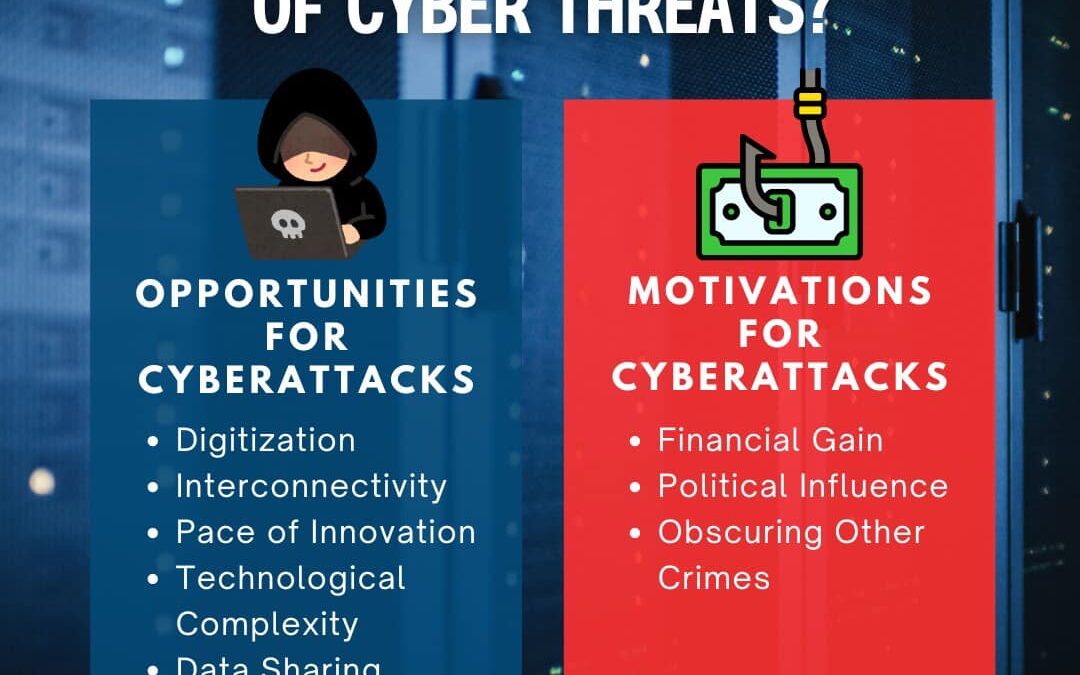
The rise of cyber threats is driven by both opportunity and motivation. As our world becomes increasingly digital and interconnected, new vulnerabilities emerge, while attackers become more sophisticated. Motivations range from financial gain to political disruption,...

by PCS | Oct 12, 2024 | 2024, Tips & Tricks
Supply chain attacks have emerged as a growing threat in the cybersecurity landscape. These attacks exploit vulnerabilities in trusted vendors’ software development or update processes, allowing attackers to inject malicious code into otherwise secure...










