
by PCS | Jan 26, 2025 | 2025, Tips & Tricks
These scams use advanced tools to analyze social media activity, crafting hyper-personalized emails that appear to come from trusted sources. Read more These sophisticated attacks grow harder to spot! Stay safe by avoiding unverified links, enabling two-factor...

by PCS | Jan 26, 2025 | 2025, Tips & Tricks
Here are 3 quick tips to kickstart your cybersecurity goals in 2025: Update all your passwords—make them long and unique. Back up your important data regularly. Stay cautious of phishing scams and suspicious links. Let’s keep your digital world as safe as your...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
The financial sector is under constant attack from evolving digital threats. Safeguarding sensitive data, preserving assets, and ensuring operational continuity aren’t just technical necessities—they’re the foundation of trust and integrity. Boost Your...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Enhance your HR team’s cybersecurity skills with our comprehensive training programs! Flexible options: self-paced, virtual, or face-to-face. Earn certificates and virtual badges upon completion. Contact us at [email protected] to safeguard your...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Online dating can be an exciting way to meet new people, but safety should always come first. Protect yourself by spotting fake profiles, verifying your matches, and avoiding any requests for personal information or financial help. #PinedaCyberSecurity...
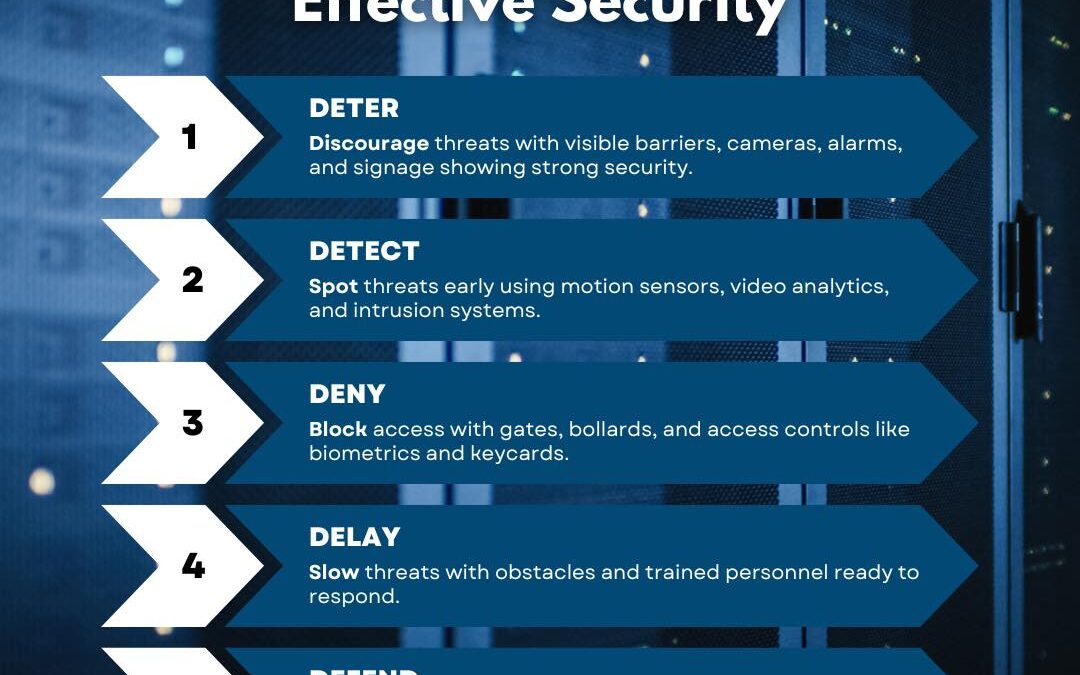
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Effective security starts with understanding the 5 Ds: Deter, Detect, Deny, Delay, and Defend. These core principles create a robust, layered defense against both physical and cyber threats. #PinedaCyberSecurity #CyberSecurityMakesSenseHere #SecurityStrategies...










