
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Attention Parents! Scammers are targeting Aussie kids on social media with fake profiles and websites that look like trusted brands. In 2024 alone, over $129,700 has been lost to these scams, with children and teens falling victim to online fraud. Stay vigilant and...
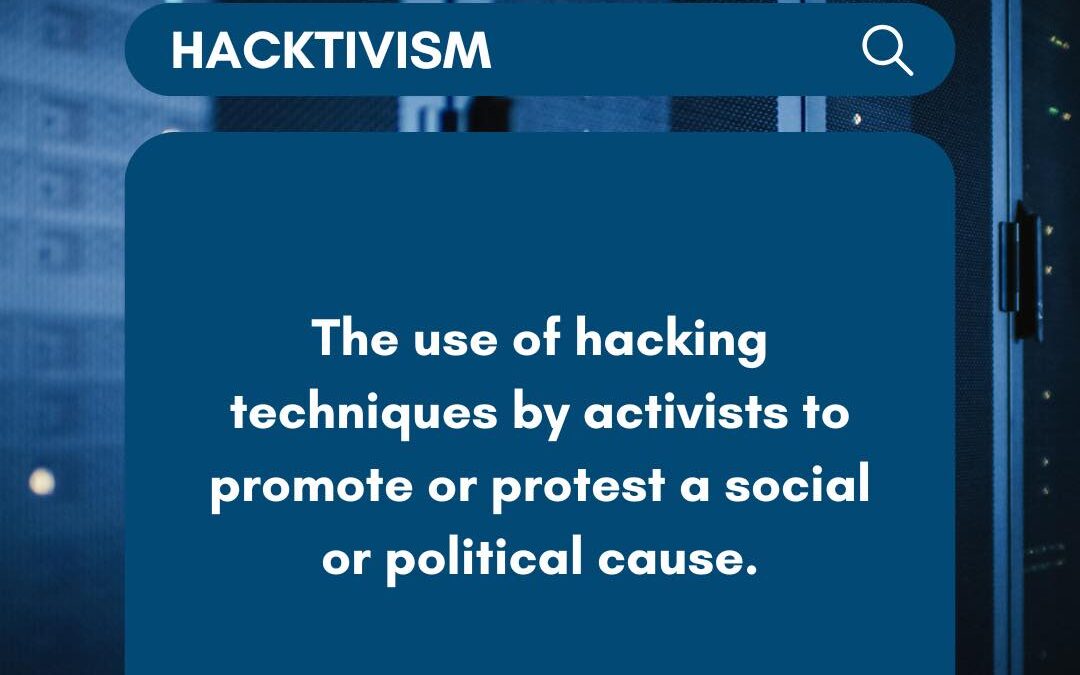
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Hacktivism represents a fusion of digital skills and activism, where individuals or groups leverage hacking to champion social or political causes. Their targets often include governments, corporations, or other significant institutions they perceive as unjust or...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
In the ever-evolving landscape of cybersecurity, understanding the different types of threat actors is crucial for staying ahead. From financially motivated cybercriminals to politically driven hacktivists and nation-state actors, the spectrum of threats is vast. Even...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Every click, every transaction, and every piece of data shared online deserves protection. Cybersecurity safeguards are the invisible shield that keeps our digital lives secure. From firewalls to encryption, these tools and techniques work tirelessly to prevent...
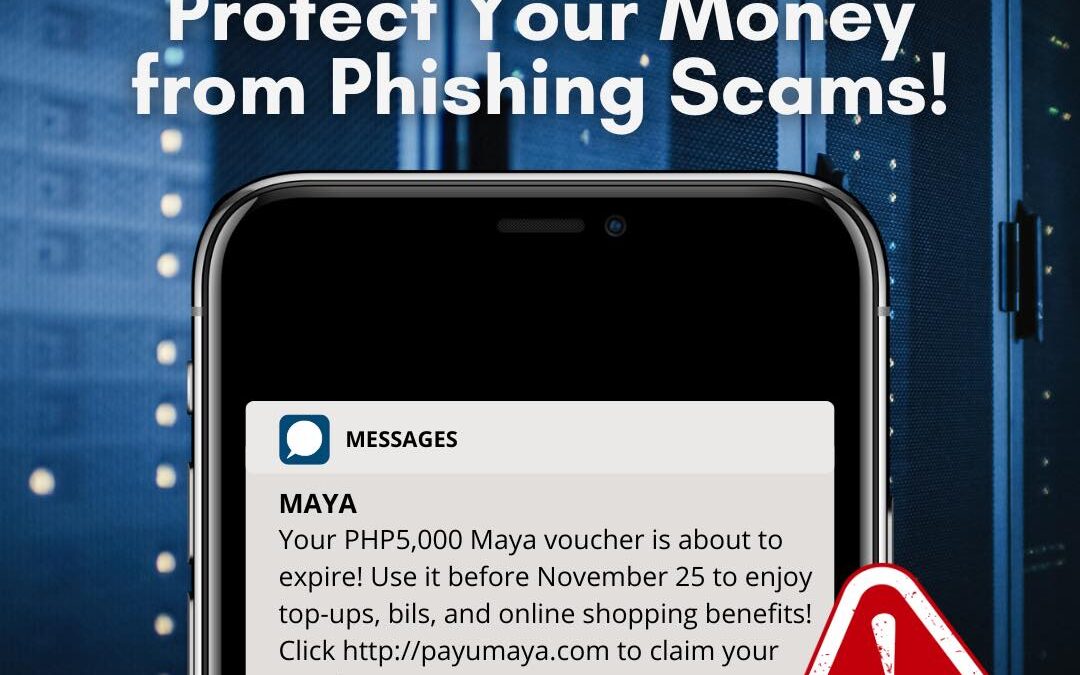
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
BEWARE OF THIS NEW SCAM! Phishing attacks are on the rise, targeting unsuspecting individuals with fake messages mimicking trusted brands like Maya. Remember, legitimate companies will NEVER ask you to click suspicious links or provide personal information via text....

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Advanced Persistent Threats (APTs) represent the pinnacle of strategic cybercrime, combining stealth, patience, and precision. These attacks often target high-value entities like government organizations or large corporations, aiming to extract sensitive data or...










