
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Data poisoning is a silent but devastating threat to businesses leveraging AI. By manipulating training data, attackers can disrupt operations, compromise decision-making, and expose organizations to severe security breaches. The implications span financial losses,...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Imagine your AI learning from a sabotaged textbook! Data poisoning sneaks false or manipulated information into the datasets that train AI and ML systems, turning once-smart models into unreliable tools. Whether adding fake data, altering existing information, or...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
A new scam on Facebook is targeting unemployed men with false promises of lucrative rewards in exchange for fatherhood. These scams lure victims with stolen photos and elaborate stories, ultimately extracting upfront payments before disappearing. Never trust...
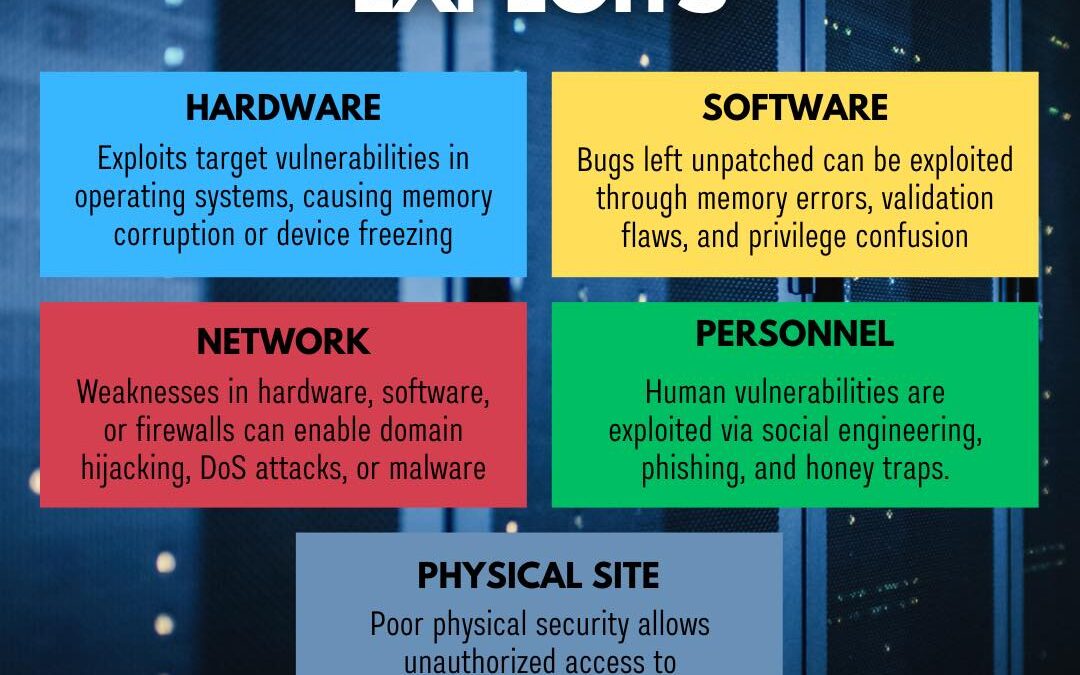
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Understanding the different types of cyber exploits is the first step in safeguarding your organization. From hardware vulnerabilities and software bugs to network gaps, personnel manipulation, and physical site breaches, cybercriminals are always on the lookout for...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Exploits are a critical tool in the hacker’s arsenal, taking advantage of software or hardware flaws to infiltrate and compromise systems. While they’re often confused with malware, exploits are the methods, not the payloads; they’re the doors left ajar that allow...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Protecting your digital privacy can be simple with the right steps. These quick tips can help you keep your online activities and personal data safe. #PinedaCyberSecurity #CyberSecurityMakesSenseHere #DigitalPrivacy #StaySafeOnline #PrivacyMatters #SafeBrowsing...










