by PCS | Dec 19, 2024 | 2024, Tips & Tricks
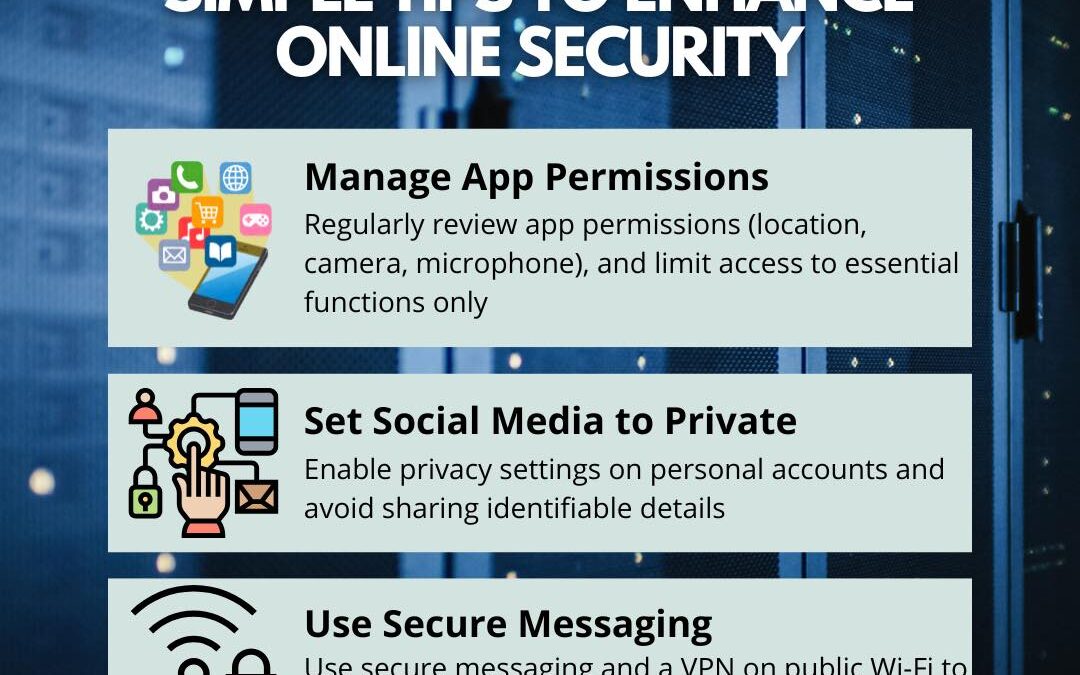
Staying safe online is essential, especially for teenagers who often use social media and apps. Small actions like managing app permissions, setting accounts to private, and using secure messaging tools can significantly reduce privacy risks. Simple adjustments lead...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Acting as a digital barrier, a firewall defends networks from unauthorized access, allowing only trusted data to pass through. Positioned between a trusted network and potential threats from external networks, it scrutinizes every data packet that attempts to enter or...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
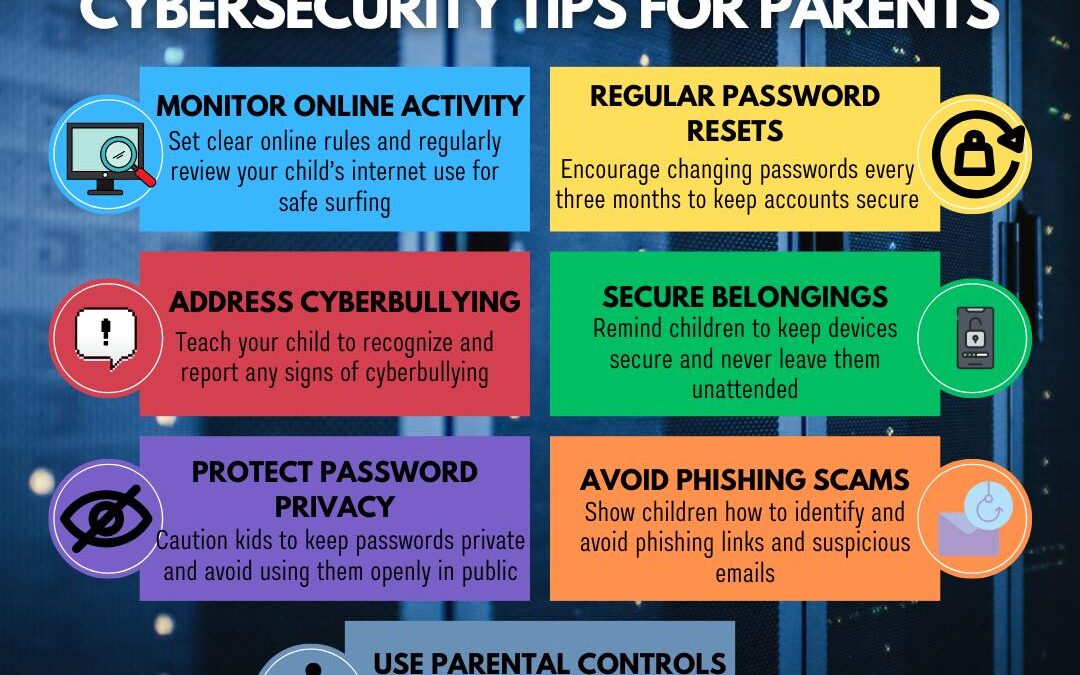
Protecting children online is more important than ever in today’s digital age. By setting boundaries, regularly updating passwords, and discussing online safety measures, parents can help children navigate the internet responsibly. Awareness of cyberbullying,...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
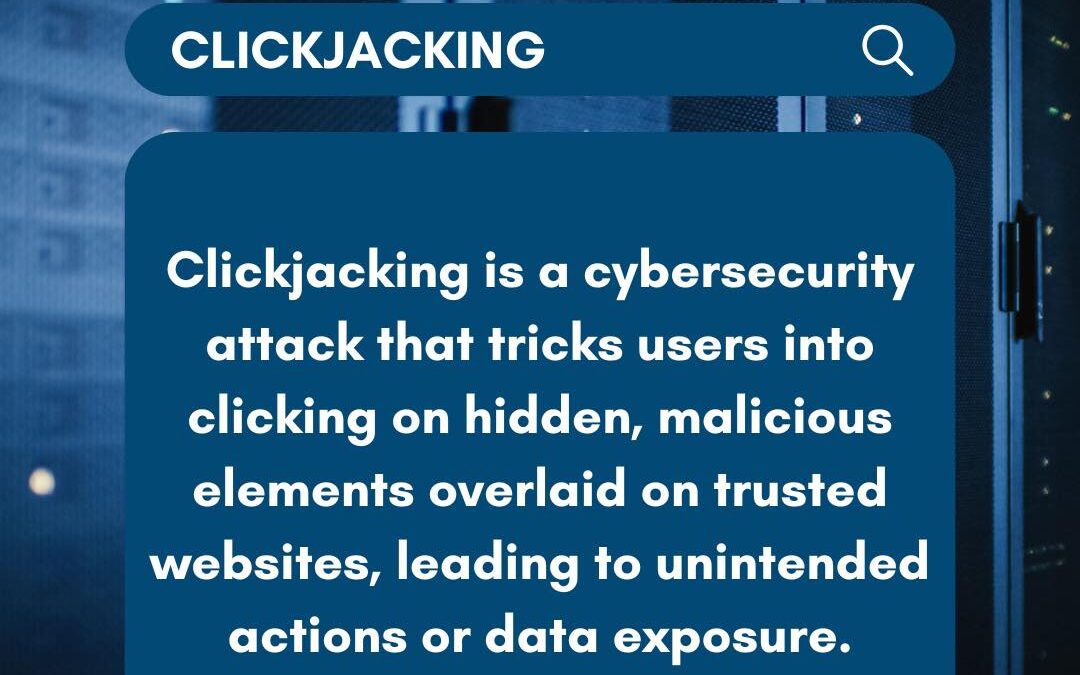
Clickjacking is a sneaky cyber attack where a user believes they’re interacting with a trusted website, but they’re actually clicking on hidden elements placed by an attacker. This tactic can range from simple pranks, like generating fake likes on social media (known...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Adding an extra layer of security, two-factor authentication (2FA) helps protect sensitive data by requiring more than just a password. With 2FA, users provide something they know—like a password or PIN—and something they have, such as a smartphone code or even a...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
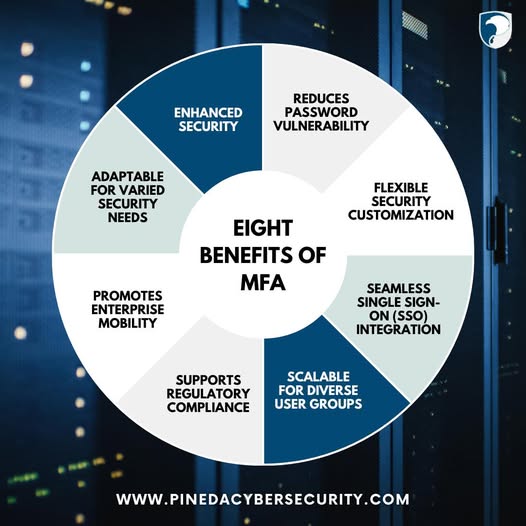
Multi-factor authentication (MFA) enhances security by adding layers of protection, making it harder for cybercriminals to breach accounts even if passwords are compromised. With the flexibility to customize security settings, MFA integrates seamlessly with Single...










