
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
MFA is a crucial security measure in today’s digital landscape. With just a password, accounts are vulnerable to attacks, but adding another layer, like a code sent to your phone or biometric verification, makes it significantly harder for unauthorized users to gain...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
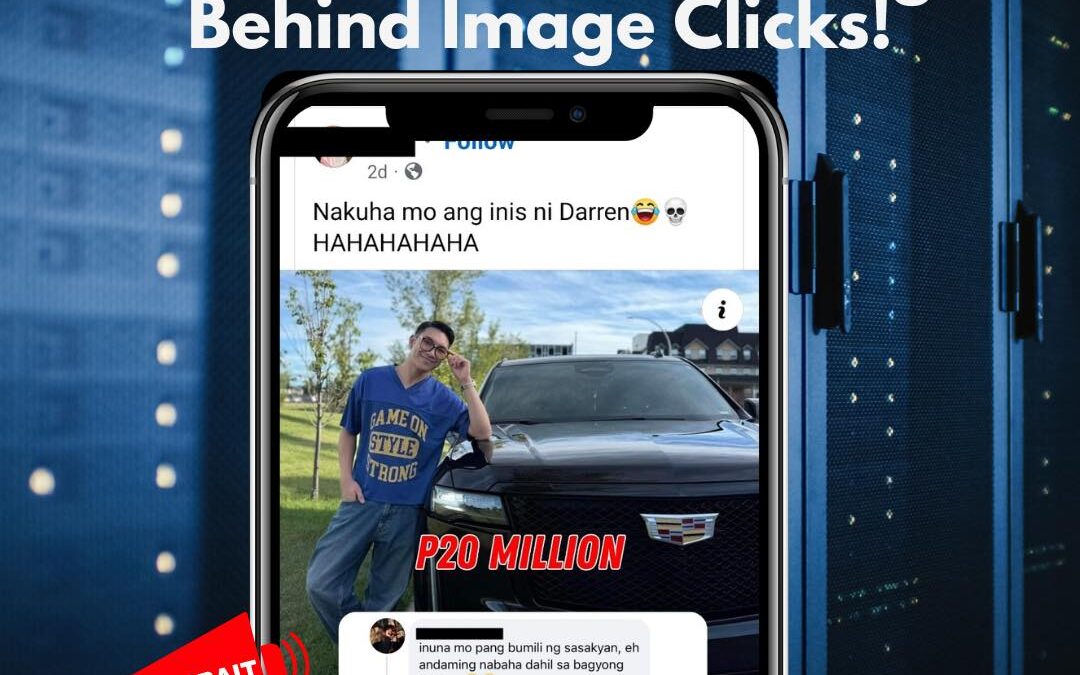
Stay vigilant! Cybercriminals are finding sneaky ways to lure users to suspicious sites through innocent-looking images. Recently, a scam using fake links to popular sites has been tricking users on social media. If you click an image and end up on an unrelated page,...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
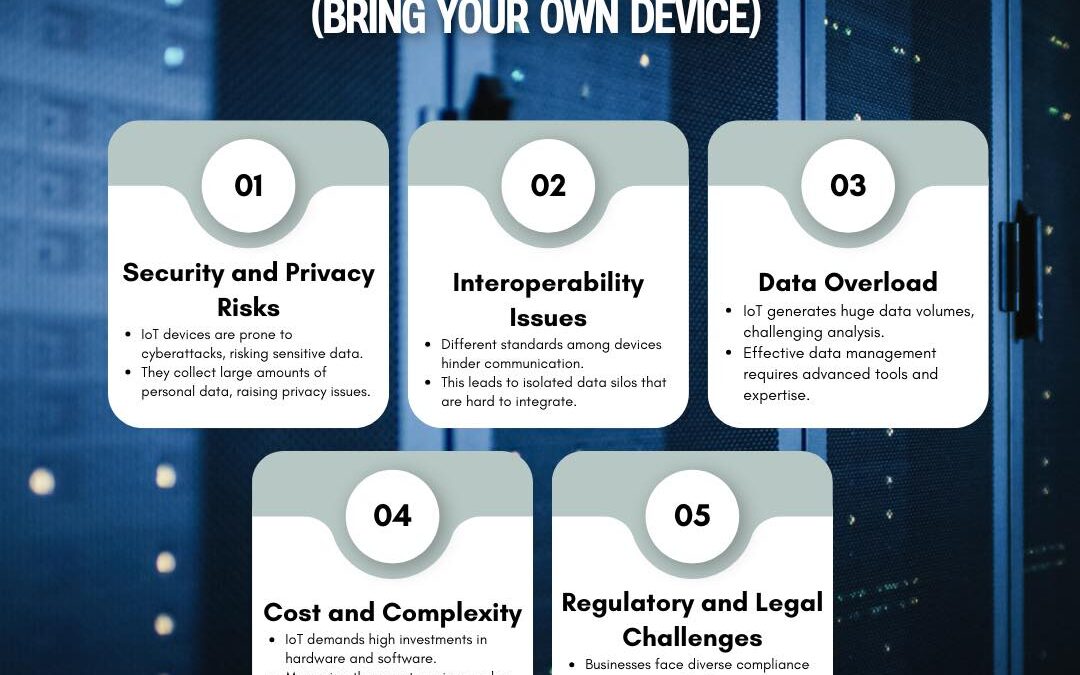
The Internet of Things (IoT) is transforming industries and daily life, but it also brings unique risks and challenges that demand attention. From security vulnerabilities and data overload to regulatory concerns, businesses need to navigate these complexities to...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
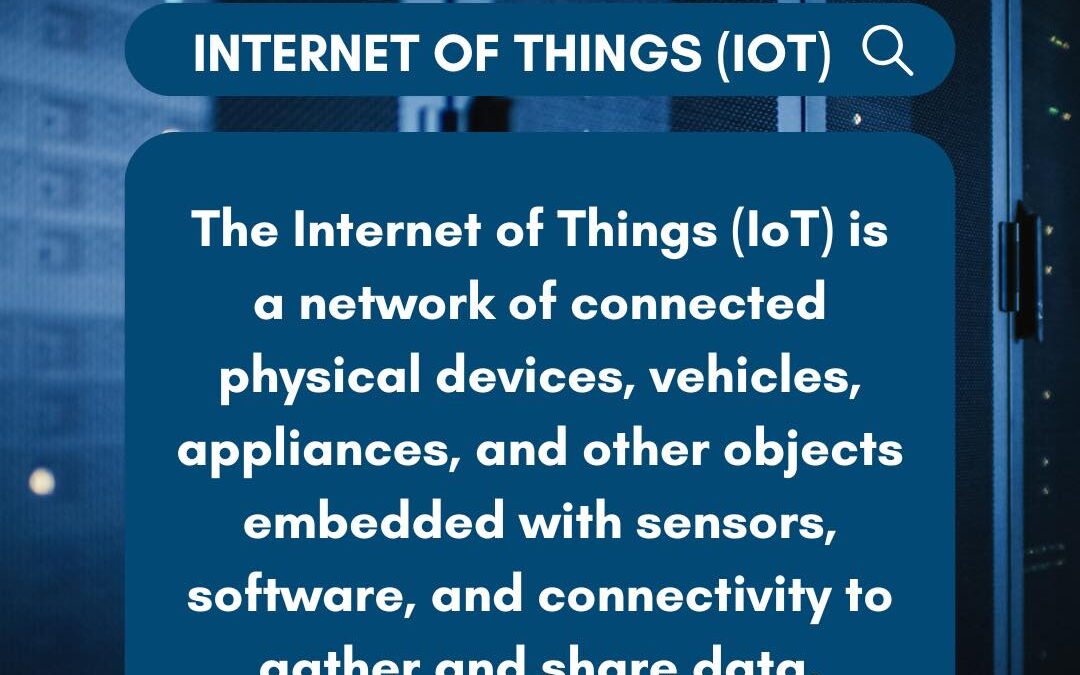
Imagine a world where devices—from home appliances to industrial machines—are constantly communicating, sharing real-time data, and automating tasks. IoT brings this to life, creating an interconnected network that improves efficiency, convenience, and insights across...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
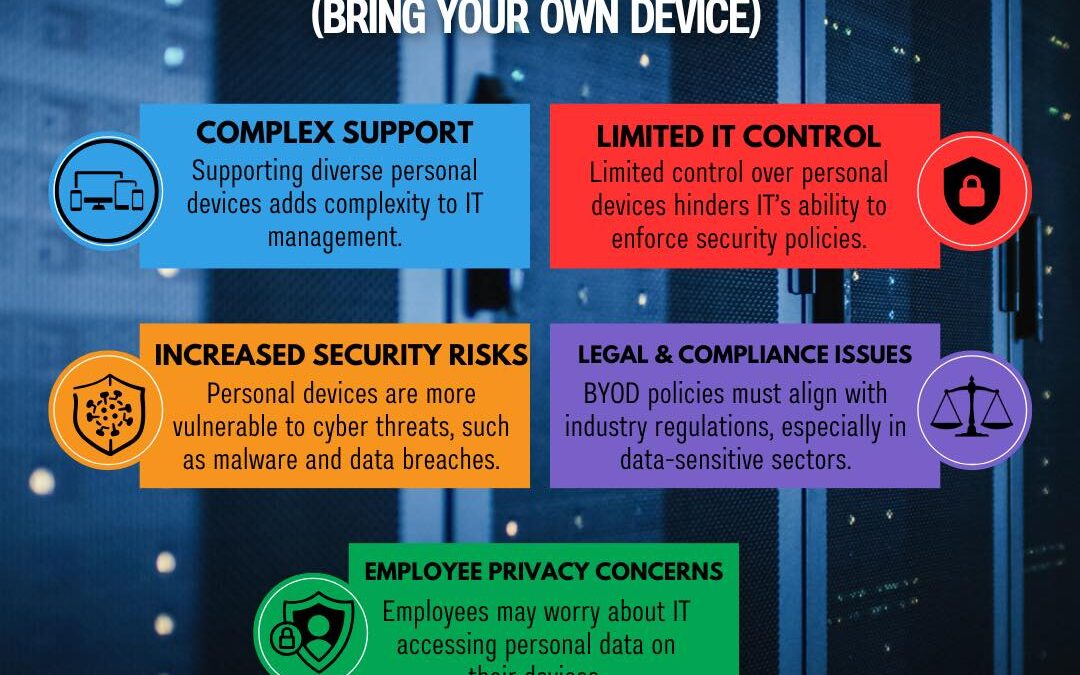
Bring Your Own Device (BYOD) policies offer many benefits, but they also introduce specific challenges that organizations must navigate carefully. From complex IT support to increased security risks, each aspect of BYOD presents unique issues that require thoughtful...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
The Bring Your Own Device (BYOD) policy has evolved to accommodate today’s flexible work environments, particularly with the shift to remote and hybrid work. Originally focusing on smartphones, BYOD policies now cover various devices as employees increasingly use...










