by PCS | Dec 19, 2024 | 2024, Tips & Tricks
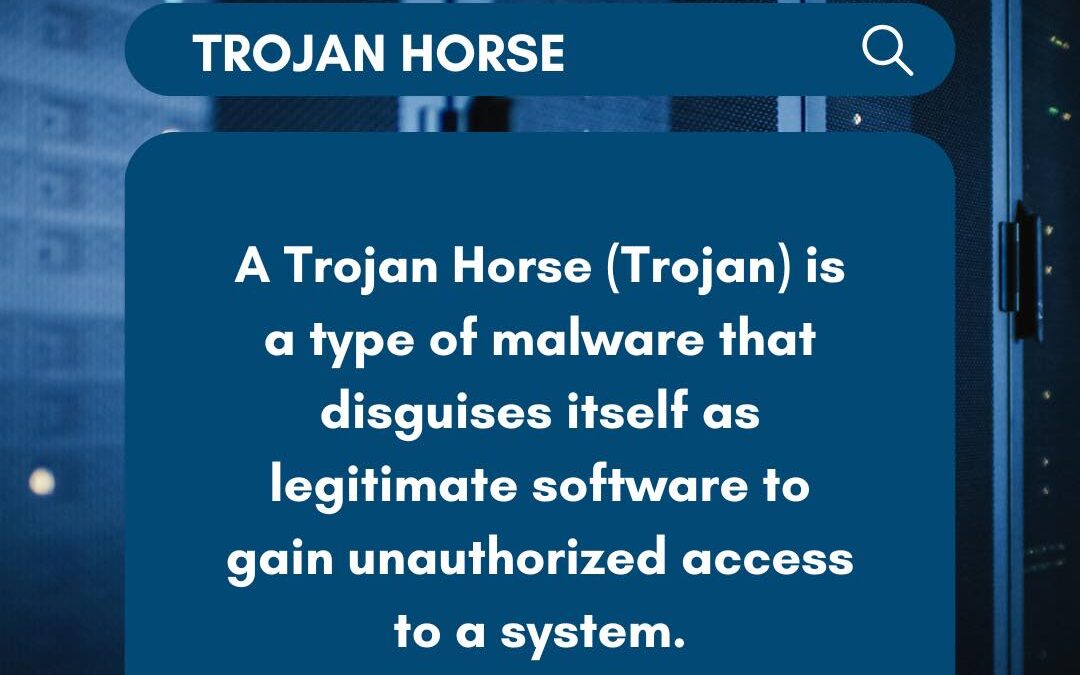
A Trojan Horse is a classic tool in a hacker’s arsenal, slipping past defenses by pretending to be trusted software. Once inside, it can wreak havoc—exporting data, altering files, or even deleting crucial information. Trojans often find their way in through enticing...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
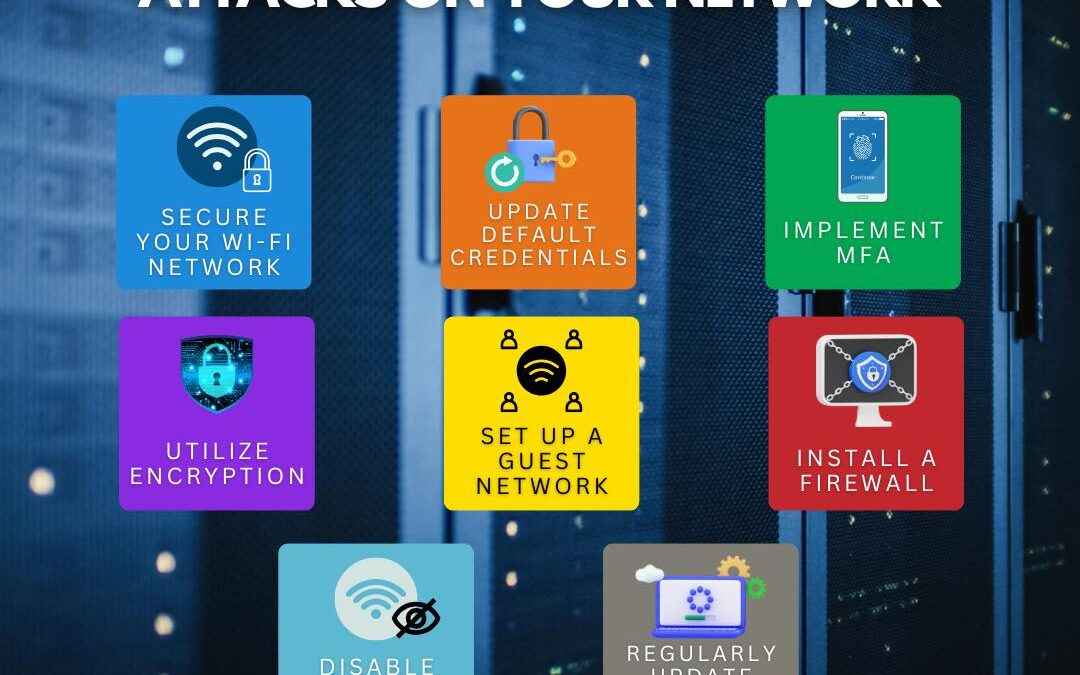
Protecting your network from wardriving attacks starts with simple, proactive steps. By securing your Wi-Fi, updating credentials, and utilizing encryption, you can significantly reduce the risk of unauthorized access. Setting up a guest network, enabling multi-factor...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
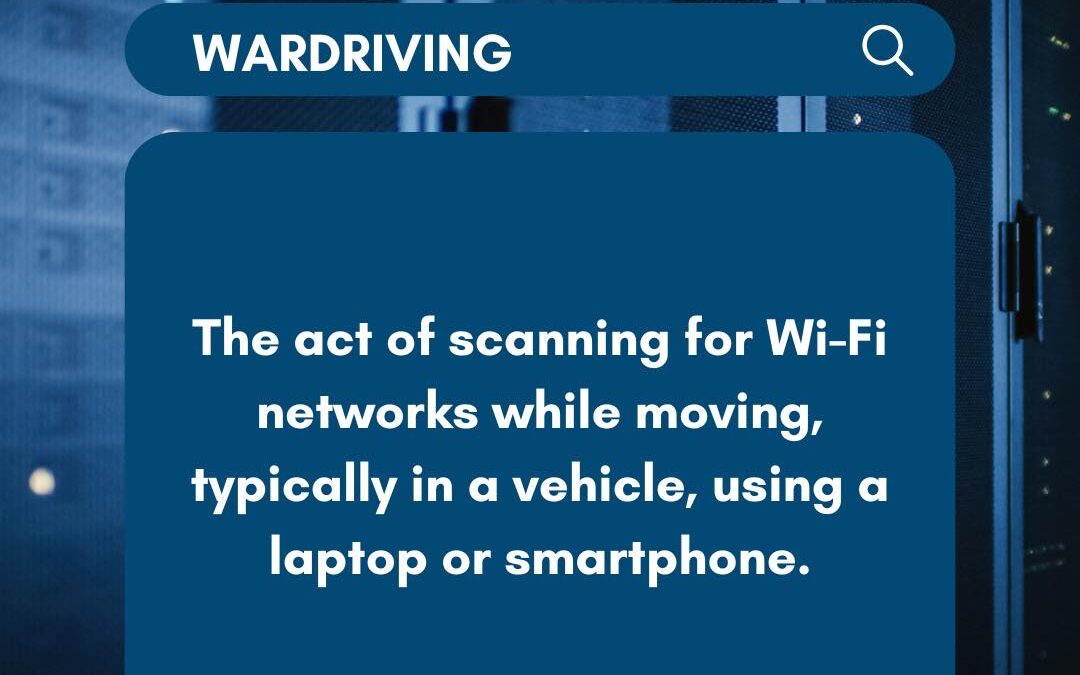
Wardriving involves driving around with a device to detect and map wireless networks, often done to find unsecured or poorly secured connections. While some may do it for research or mapping purposes, others might exploit vulnerabilities for malicious intent, such as...
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
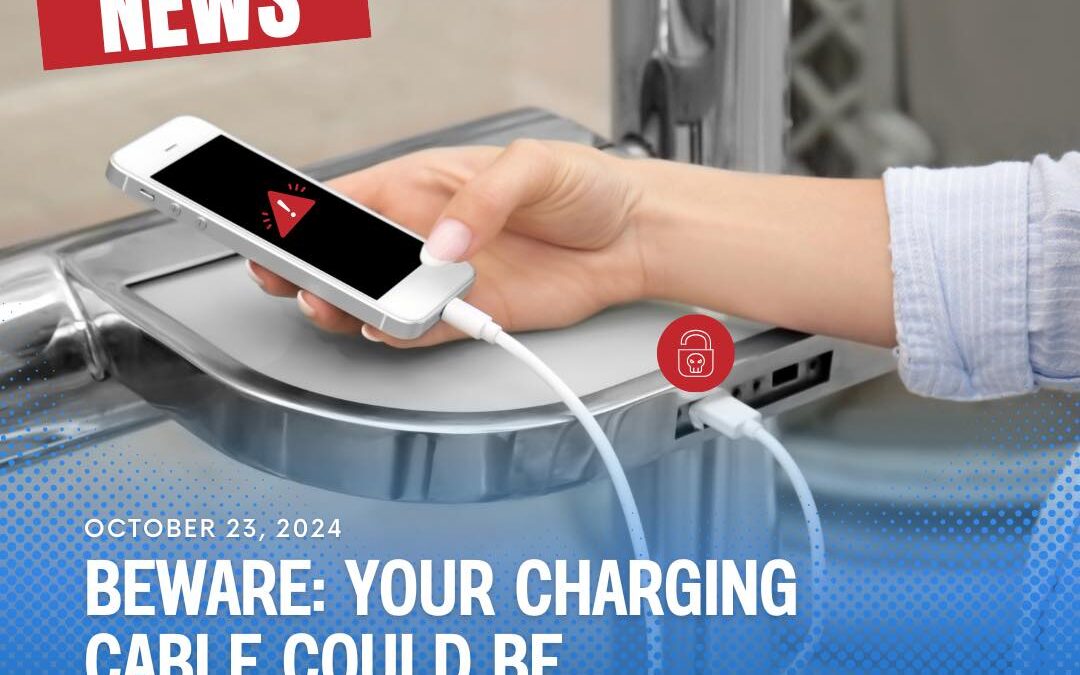
With the rise of sophisticated hacking tools, even something as common as a phone charging cable can become a cybersecurity threat. The Hak5 O.MG Cable demonstrates how easily vulnerabilities can be exploited, turning ordinary accessories into malicious devices. It’s...

by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Worms are one of the most insidious forms of malware, capable of replicating and distributing themselves across networks without any user action. Unlike viruses, worms don’t need to attach themselves to a program or file to spread, making them particularly efficient...
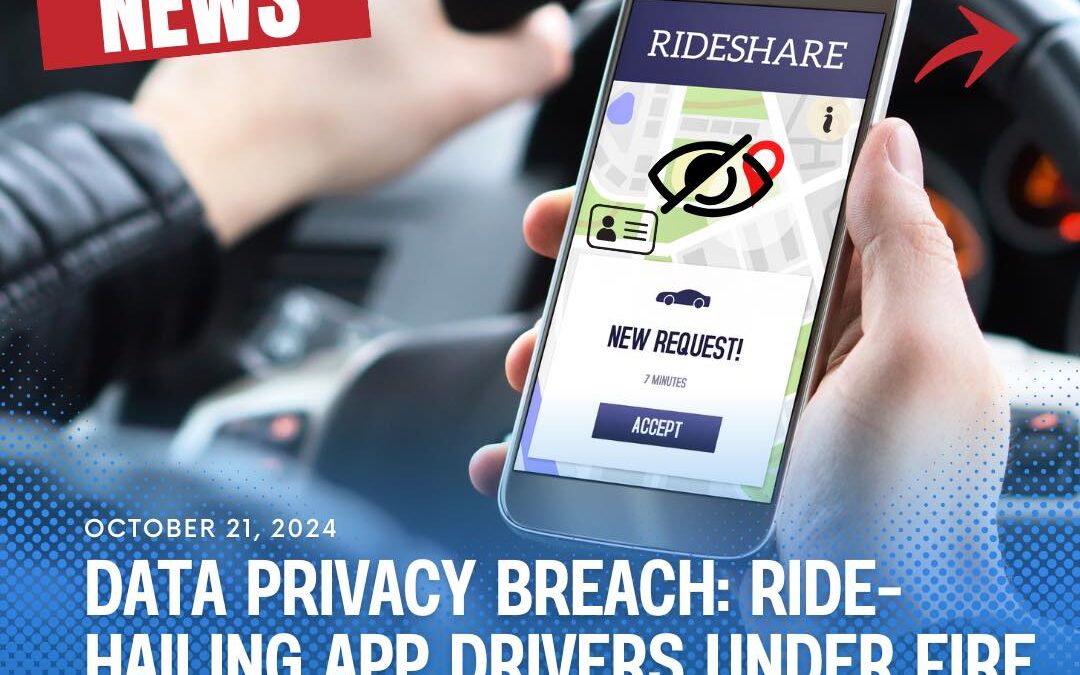
by PCS | Dec 19, 2024 | 2024, Tips & Tricks
Recent reports have highlighted alarming privacy issues within the ride-hailing industry. Some drivers from the inDrive platform were caught sharing sensitive passenger information, including photos, trip routes, and payment details, on social media. This breach of...










