
by PCS | Sep 5, 2024 | 2024, 2024, Tips & Tricks, Updates
Data remanence refers to the leftover data that persists even after deletion, posing a significant security risk. To effectively mitigate the threat of unauthorized data recovery, it’s crucial to address this issue properly. Among the methods to deal with data...

by PCS | Sep 5, 2024 | 2024, 2024, Tips & Tricks, Updates
A strong Risk Management Strategy is essential to achieving the goals of any organization’s risk management objectives. The primary goals are to recognize all possible risks and reduce them to an acceptable level, ensuring the organization remains secure and...

by PCS | Sep 5, 2024 | 2024, Updates
On Ninoy Aquino Day, we remember the life and sacrifice of a man who stood for democracy and freedom. His assassination on August 21, 1983, marked a turning point in Philippine history, inspiring a nation to fight for its rights. Let us honor his legacy and continue...
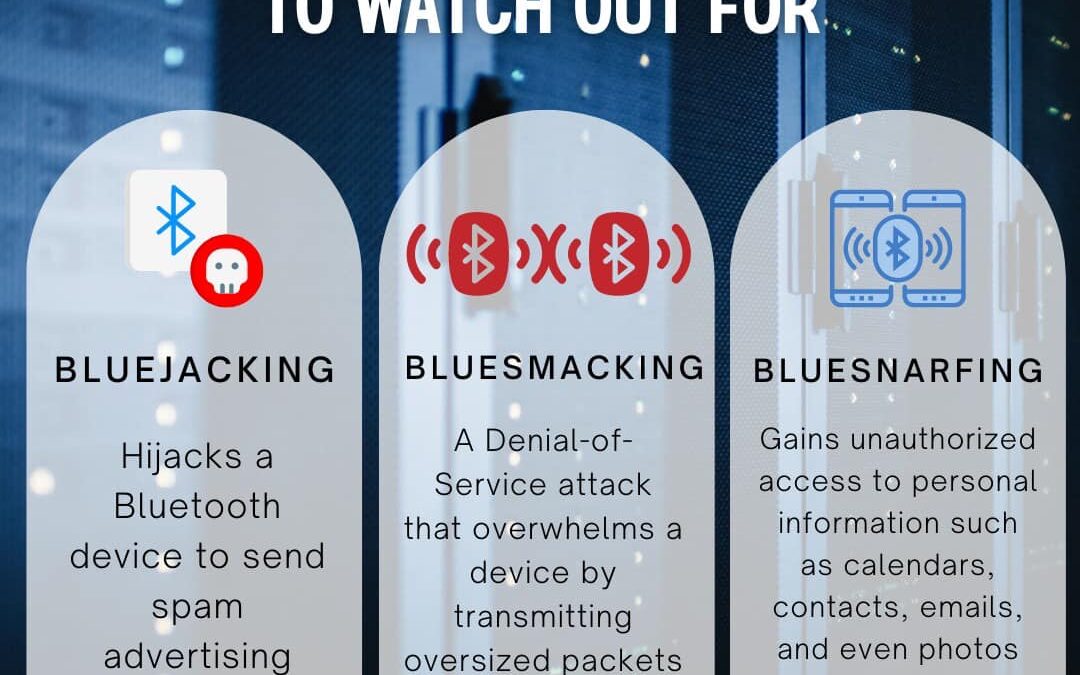
by PCS | Sep 5, 2024 | 2024, 2024, Tips & Tricks, Updates
Bluetooth technology offers incredible convenience, allowing seamless connectivity between devices, but it also comes with certain risks. This convenience can expose your devices to various security threats. Here are some of the most common Bluetooth attacks. Stay...

by PCS | Sep 5, 2024 | 2024, 2024, Tips & Tricks, Updates
CONSENT in CYBERSECURITY should be FREELY GIVEN, allowing you to choose what data you share. It should be REVERSIBLE, giving you the power to change your mind and retract permissions. It must be INFORMED, making sure you understand the risks and benefits. It should be...

by PCS | Sep 5, 2024 | 2024, Updates
The National Privacy Commission (NPC) has issued a crucial circular outlining the guidelines for CCTV systems, ensuring that their use aligns with the Data Privacy Act of 2012. This circular emphasizes the importance of protecting individuals’ privacy by setting...










