by PCS | Sep 5, 2024 | 2024, Updates
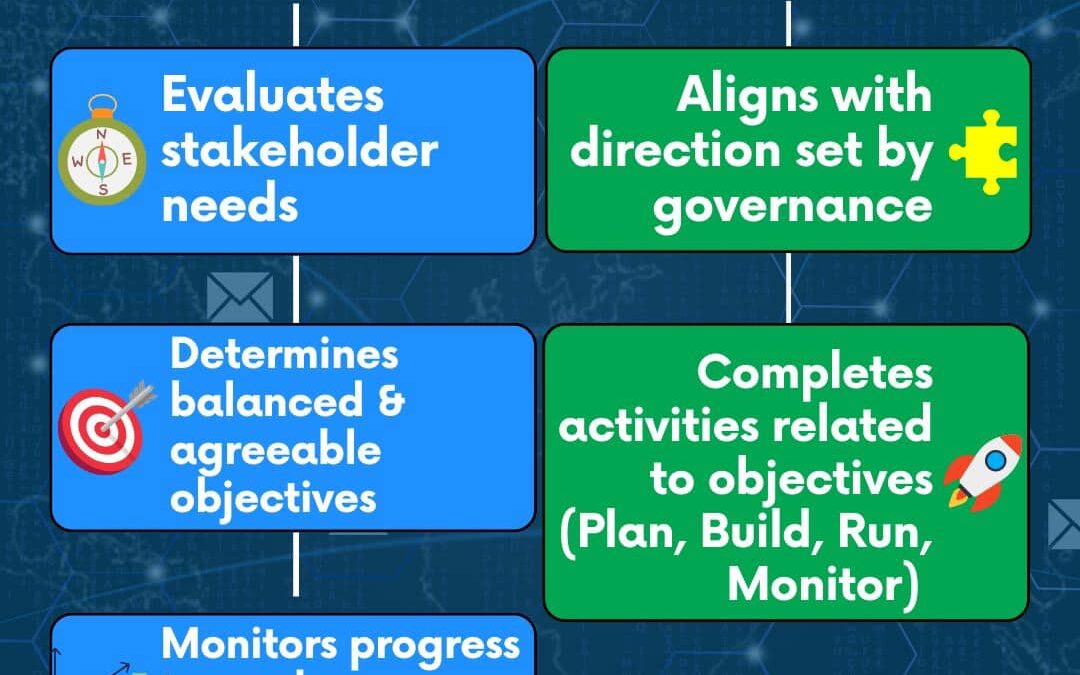
This diagram highlights the critical distinction between governance and management in Information Security Governance. GOVERNANCE focuses on setting the direction by evaluating stakeholder needs, determining objectives, and monitoring progress. MANAGEMENT, on the...

by PCS | Sep 5, 2024 | 2024, Updates
Today’s #CybersecurityTerm is ‘Checksum’—a crucial tool in safeguarding data integrity. Whether you’re dealing with sensitive documents or important software updates, understanding and using checksums is key to maintaining trust in your digital...

by PCS | Sep 5, 2024 | 2024, Updates
Effective Information Security Governance is crucial for protecting organizational assets and aligning security initiatives with business objectives. By focusing on these six key outcomes, we ensure that security measures are both efficient and effective, driving...

by PCS | Sep 5, 2024 | 2024, Updates
In today’s digital world, it’s crucial for schools and teachers to prioritize student privacy, especially when sharing images or screenshots from online classes. Under the Data Privacy Act (DPA), using student names and photos requires a lawful basis,...

by PCS | Sep 5, 2024 | 2024, Updates
We all know about the millions of pesos in prizes and lifetime rewards being offered by brands to our double olympic gold medalist. Beware though of the rampant Olympic online scams, including a fake page of gymnast Carlos Yulo, promising cash rewards for signing up....
by PCS | Sep 5, 2024 | 2024, Updates
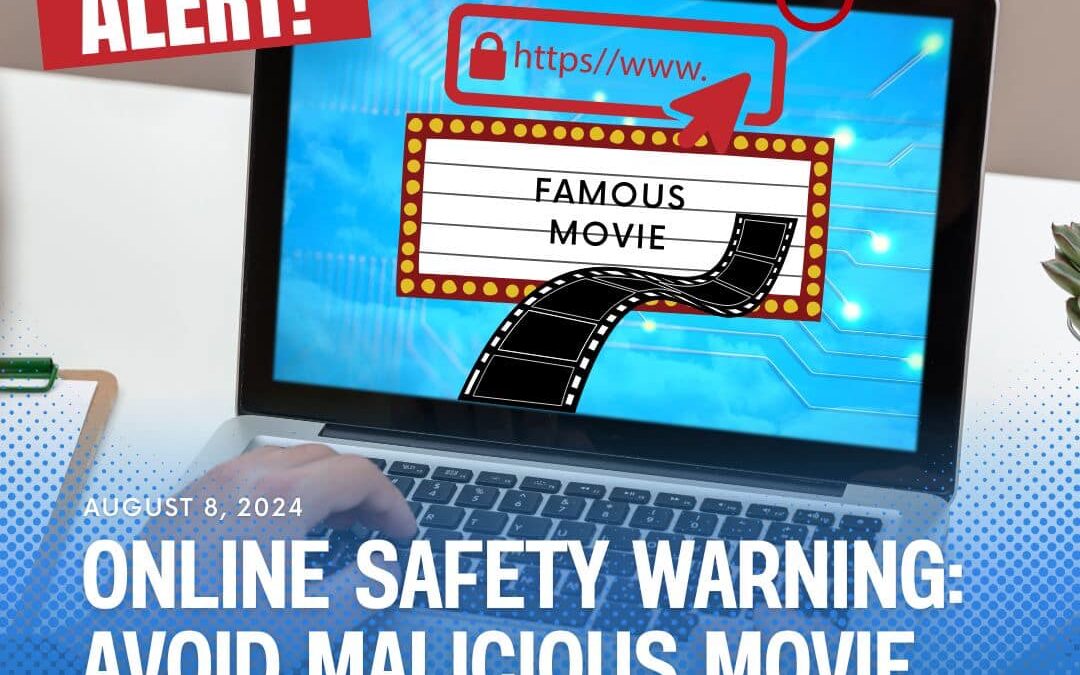
WARNING: Be cautious of clickbait videos that promise movie titles but fail to deliver! These posts often lead to malicious websites that can compromise your privacy and security. Always verify the source before clicking any links and report suspicious content to keep...










