
by PCS | Sep 5, 2024 | 2024, 2024, Tips & Tricks, Updates
Understanding the difference between Validation and Verification is crucial in building successful applications and products. Ensuring the right product is being built and then confirming it is built correctly can save time, resources, and ensure higher quality...

by PCS | Sep 5, 2024 | 2024, 2024, Tips & Tricks, Updates
Understanding the fundamental principles of Identity and Access Management (IAM) is crucial for cybersecurity professionals. This diagram outlines the four key principles of IAM: Identification/Assertion: Verifying an individual’s identity and assigning a unique...
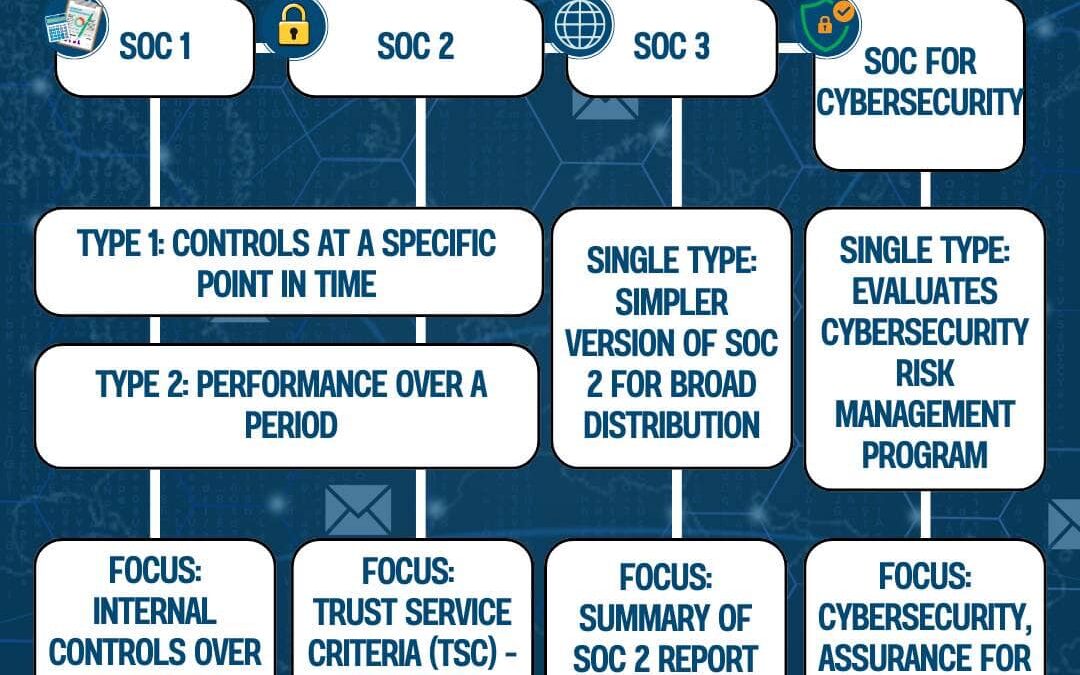
by PCS | Aug 30, 2024 | 2024, 2024, Tips & Tricks, Updates
This diagram illustrates the different types of SOC (Service Organization Control) reports, detailing their purposes and focus areas. SOC 1 reports assess the internal controls over financial reporting (ICFR) and are divided into Type 1 (point in time) and Type 2...

by PCS | Aug 30, 2024 | 2024, 2024, Tips & Tricks, Updates
Threat modeling takes an attacker’s perspective to identify vulnerabilities in your environment, system, or application. STRIDE, a popular threat model, categorizes security threats into six key areas: Spoofing:Impersonating someone or something...
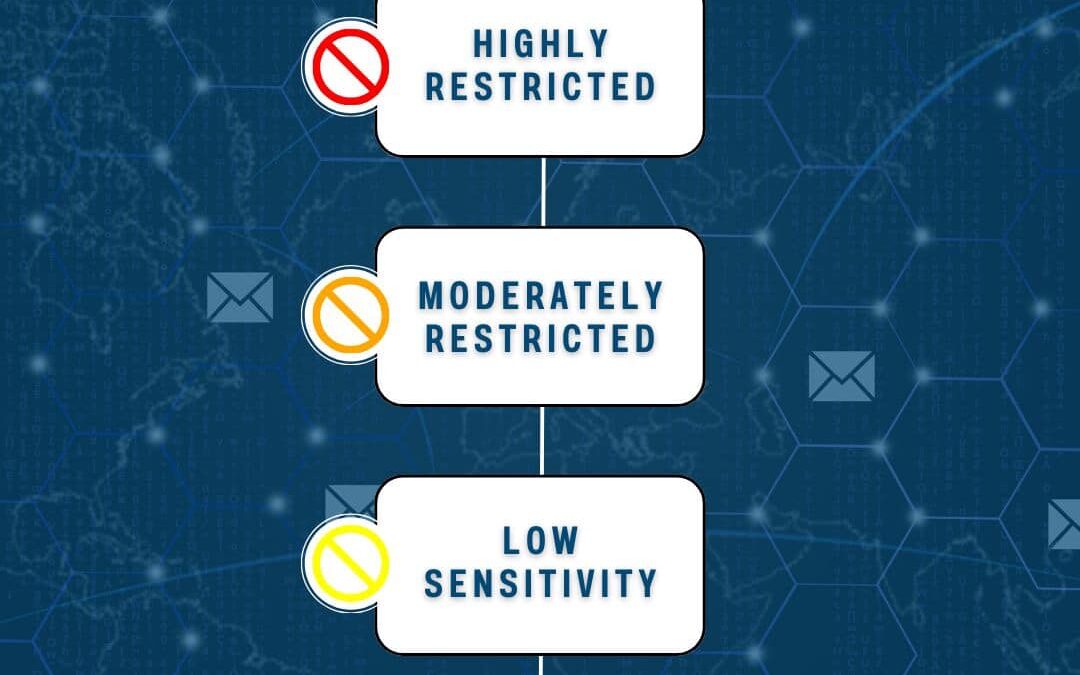
by PCS | Aug 30, 2024 | 2024, 2024, Tips & Tricks, Updates
Understanding Data Sensitivity Levels is crucial for effective asset security management. This flowchart breaks down the different levels, and explains their potential impacts.Highly Restricted:Compromise could risk the organization’s future, cause substantial...

by PCS | Aug 30, 2024 | 2024, 2024, Tips & Tricks, Updates
This review outlines the six fundamental principles established in Article 5 of the GDPR, guiding the use of personal data: Lawfulness,Fairness,and Transparency:Data must be collected, processed, used, shared, stored, and destroyed in a manner that is legal, fair,...










