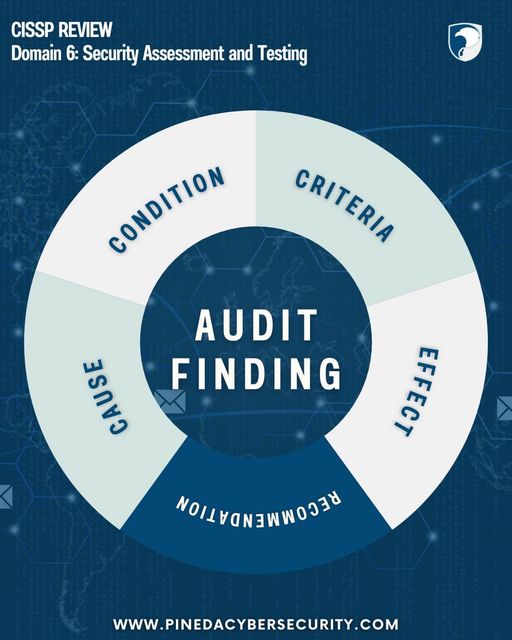
by PCS | Aug 30, 2024 | 2024, 2024, Tips & Tricks, Updates
Understanding the core elements of an audit is crucial for effective security assessment and testing. This diagram breaks down the key components of a finding: Condition:A description of the audit’s findings.Criteria:The benchmarks used to evaluate the...
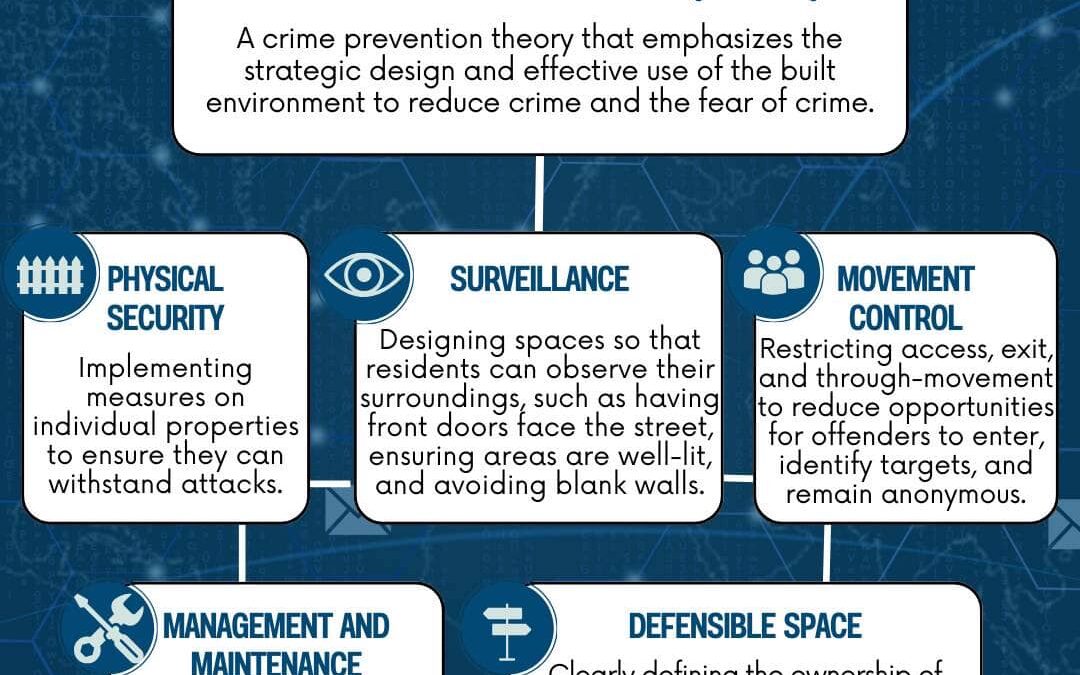
by PCS | Aug 30, 2024 | 2024, 2024, Tips & Tricks, Updates
Here’s how CPTED can transform our communities. By integrating strategic design and effective use of our environments, we can significantly reduce crime and enhance safety. This theory offers practical insights to make our neighborhoods more secure and welcoming. In...

by PCS | Aug 30, 2024 | 2024, 2024, Tips & Tricks, Updates
Introducing the ISC2 Code of Ethics – a cornerstone for all CISSP professionals. These guiding principles ensure integrity, competence, and public trust within the cybersecurity community. Here’s an essential review to reinforce your commitment to ethical practices in...
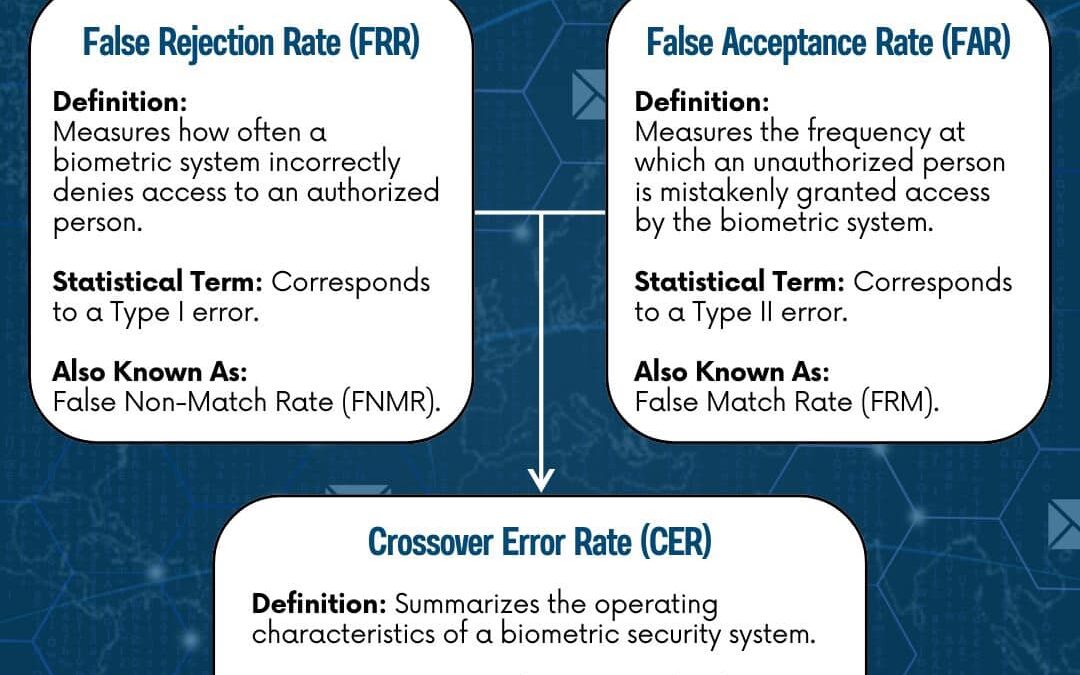
by PCS | Aug 30, 2024 | 2024, 2024, Tips & Tricks, Updates
Understanding biometric security is crucial for any cybersecurity professional. Today, let’s look into the key concepts of False Acceptance Rate (FAR), False Rejection Rate (FRR), and Crossover Error Rate (CER). #PinedaCyberSecurity #CyberSecurityMakesSenseHere...

by PCS | Aug 30, 2024 | 2024, Updates
Cybersecurity Alert! As artificial intelligence becomes more widespread, NIST and security leaders warn of an increase in poisoning attacks targeting AI systems. These attacks include availability poisoning, targeted poisoning, backdoor poisoning, and model poisoning,...

by PCS | Aug 30, 2024 | 2024, Updates
At Pineda Cybersecurity, we believe that “Cybersecurity Makes Sense Here®.” We are committed to protecting your digital landscape. Stay informed with the latest cybersecurity updates and tips by following our page. Visit www.pinedacybersecurity.com to...










