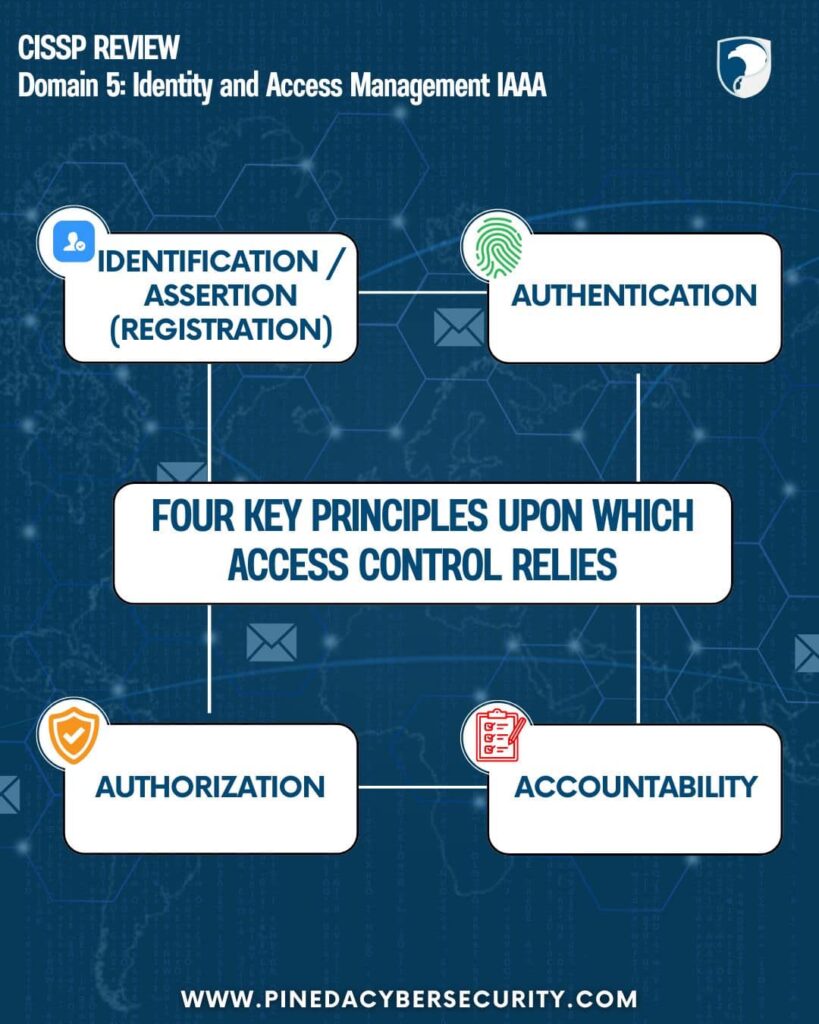
Understanding the fundamental principles of Identity and Access Management (IAM) is crucial for cybersecurity professionals. This diagram outlines the four key principles of IAM:
![]() Identification/Assertion: Verifying an individual’s identity and assigning a unique identifier.
Identification/Assertion: Verifying an individual’s identity and assigning a unique identifier.
![]() Authentication: Verifying the user’s identity using private data.
Authentication: Verifying the user’s identity using private data.
![]() Authorization: Defining and monitoring resources a user is allowed to access.
Authorization: Defining and monitoring resources a user is allowed to access.
![]() Accountability: Ensuring actions can be traced back to the responsible individual, primarily through logging.
Accountability: Ensuring actions can be traced back to the responsible individual, primarily through logging.
Master these concepts to enhance your security strategy and protect your organization’s assets
#PinedaCyberSecurity #CyberSecurityMakesSenseHere #CISSP #CyberSecurity #IAM #AccessControl #IdentityManagement #SecurityStrategy #Authentication #Authorization #Accountability #CyberSecurityTraining #InfoSec