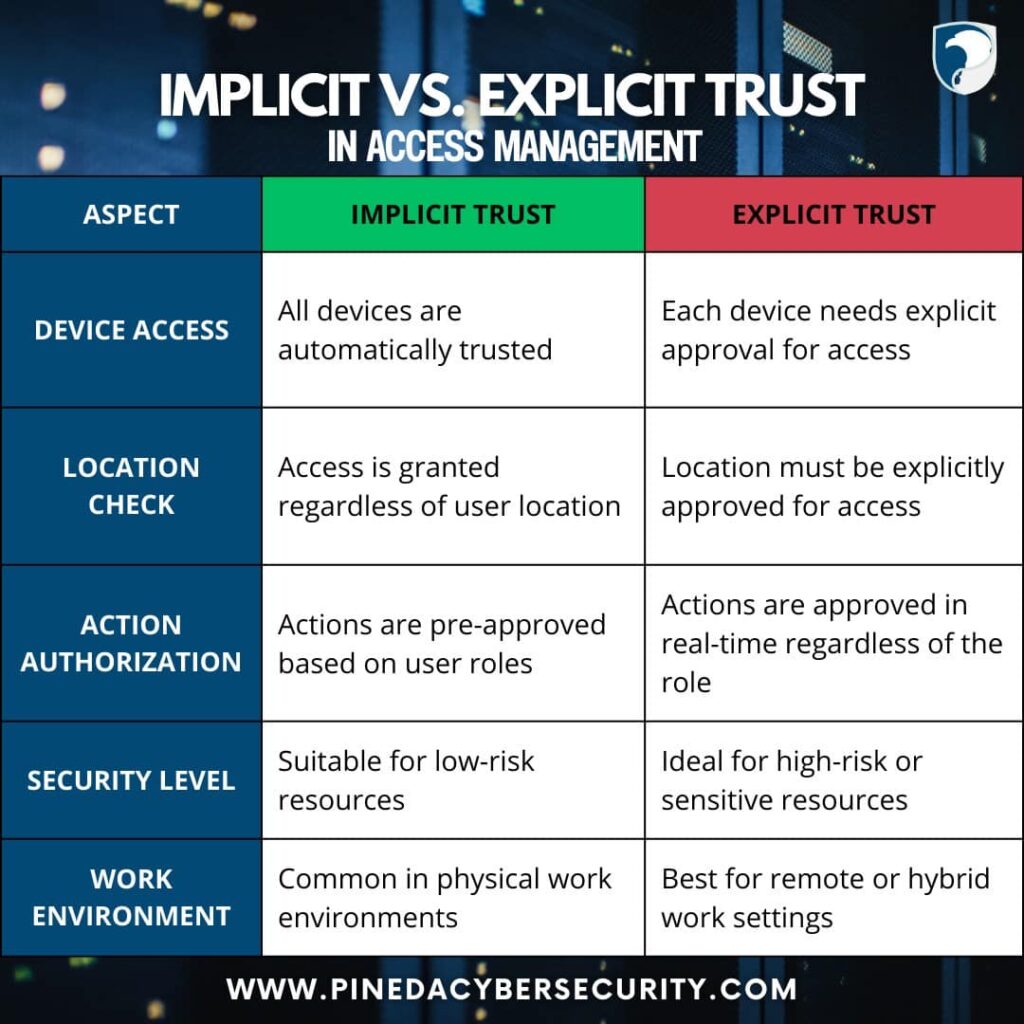
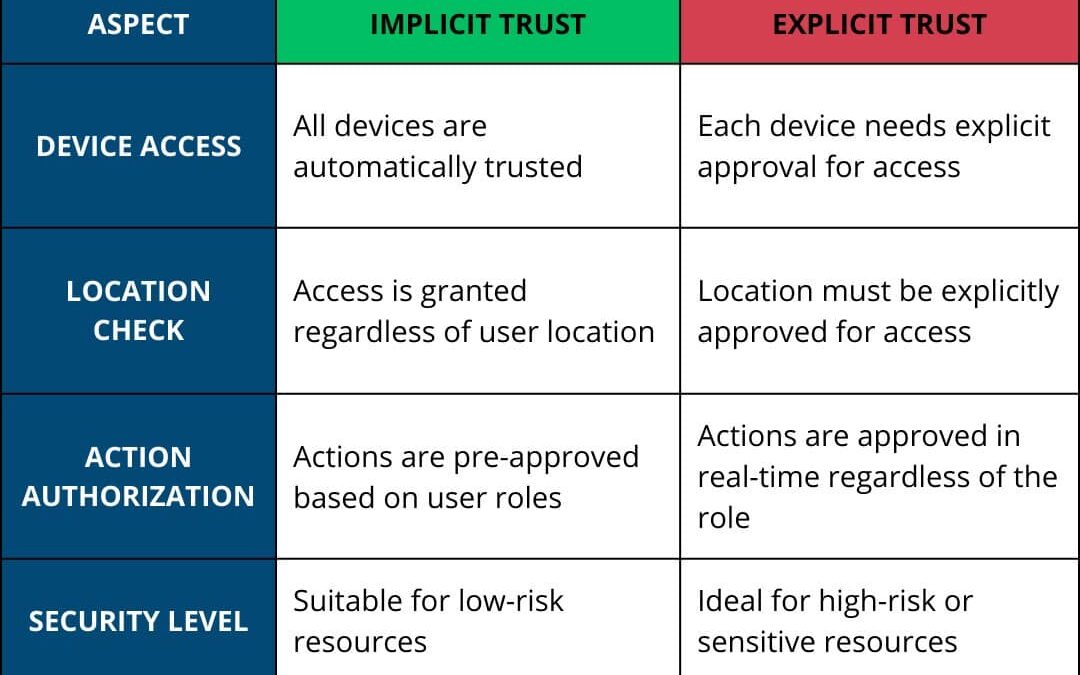
In access management, implicit trust operates under the assumption that everyone in the system is trustworthy, allowing unrestricted access until proven otherwise.
In contrast, explicit trust requires continuous verification, demanding users to prove their identity and justify access each time. Explicit trust is particularly crucial in hybrid or remote work environments where sensitive data and high-risk resources are involved.
By adopting explicit trust, organizations can reduce vulnerabilities and limit unauthorized lateral movement in their networks, making it essential for implementing Zero Trust security models.
#PinedaCyberSecurity #CyberSecurityMakesSenseHere #AccessManagement #ZeroTrust #Cybersecurity #ImplicitTrust #ExplicitTrust #RemoteWorkSecurity #HybridWorkplace #DeviceSecurity #DataProtection #RiskManagement