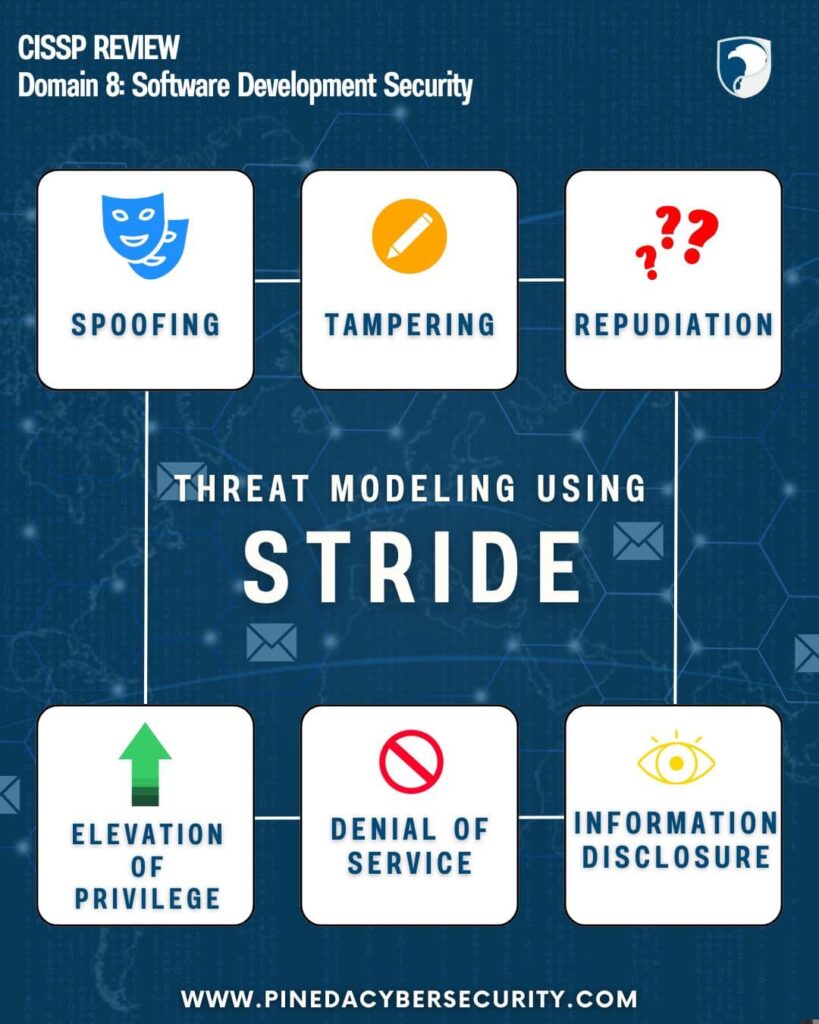
Threat modeling takes an attacker’s perspective to identify vulnerabilities in your environment, system, or application. STRIDE, a popular threat model, categorizes security threats into six key areas:
Spoofing:Impersonating someone or something else.
Tampering:Modifying data, code, or other assets.
Repudiation:Denying the performance of an action.
Information Disclosure:Exposing unauthorized information
Denial of service:Degrading or exhausting services.
Elevation Of Privilege:Gaining unauthorized privileged access
By decomposing a system into relevant components, analyzing them for threats, and identifying mitigations, security professionals can better protect against potential attacks.
Other models such as PASTA, Linddun, and Trike also aim to enhance security.
#PinedaCyberSecurity #CyberSecurityMakesSenseHere #CISSP #CyberSecurity #ThreatModeling #STRIDE #InfoSec #DataProtection #CyberSecurityTraining #ITSecurity #CISSPReview #TechSecurity